In this blog we are going to discuss email spoofing, and how can the organization prevent this attack.
Email Spoofing is a common technique that fraudsters are using for Social Engineering, phishing, or spreading malware.
In this technique, the fraudster sends an email on behalf of others by using an email address.
However, Spoofing the sender’s address makes an email legitimate and increases the likelihood of someone opening an email or its attachments.
As per the survey conducted by Forbes magazine, Fraudsters send around 1.3 Billion spoofing emails every single day.
This is because the sending email is based on the SMTP protocol that carries the message and is not concerned with the sender’s email address.
Therefore, here are some powerful tools/records that can help you fight against email spoofing.
Email spoofing protection
Add SPF (Sender Policy Framework) Record:
SPF is used for email verification and authentication deals with email spoofing. However, SPF contains the list of allowed IP addresses/hostnames that can send emails using your domain.
If the IP address/hostname doesn’t match, then the email provider will block the message.
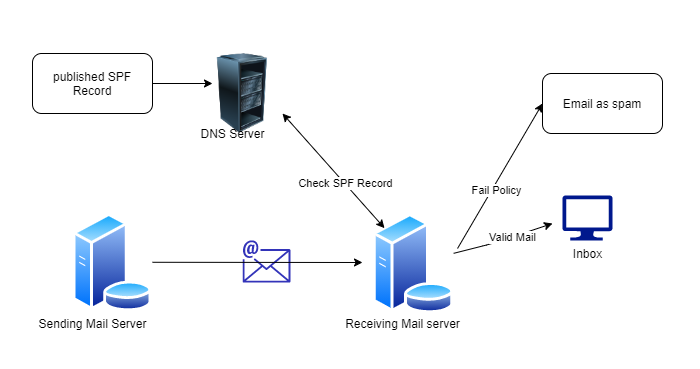
SPF Record Syntax: After defining the SPF record, it might look something like this:
|
1 |
v=spf1 ip4:xx.xx.xx.xx ip6: include:thirdpartydomain.com ~all |
- where v: define the version of the SPF record.
- ip4, ipv6: define the IP addresses that are authorized to send an email on your behalf
- include: Define the third-party organization that is used to send emails on your behalf
- ~all: If an email comes from another domain, the email will be marked as a soft fail
Add DKIM (DomainKeys Identified Mail) record:
DKIM is based on encryption, which validates the email and ensures that the message has not been modified. However, It’s a signature-based tool to implement efficient email domain authorization.
DKIM uses the email domain’s TXT record to assign a unique key to outgoing emails, which is included in the header and verified by the receiver’s server.
DKIM Record Syntax:
|
1 |
"v=DKIM1\; k=rsa\; p=jkdhfrjijjdsojfiwjddjivkjkfjvjskjskjdkdck nlsl" |
- Where v: define DKIM protocol version
- p: Define your base64 encoded public key
- k: provide the list of algorithms that can be used to decode DKIM signature (mostly use RSA algorithm)
Add DMARC (Domain-based Message Authentication, Reporting, and Conformance) record:
This is one of the advanced methods for email authentication. DMARC allows the receiver to know whether the received email is verified against the SPF and DKIM records.
It also provides a feature to take action against spoofed emails going from their domain.
DMARC Check:
| SPF | DKIM | DMARC |
| If fail ✗ | If Fail ✗ | Then fail ✗ |
| If fail ✗ | If pass ✓ | Then fail ✗ |
| If Pass ✓ | If pass ✓ | Then pass ✓ |
DMARC keeps the domain secure through a step-by-step running process.
When a sender sends an email, the SPF is verified via DNS record if matches then the verified DKIM signature is against the DNS record.
And finally, if both records do not match, depending upon DMARC policy we can take action against mail. We can define DMARC policy as
v=DMARC1; p=none; rua=mailto:[email protected]
- Where v: define the version of the DMARC record
- rua: define addresses to which aggregate feedback is to be sent
- p: define policy and its valid value can be:
- IF p=’none’: no action
- IF p=’reject’: reject all emails that fail the DMARC check
- IF p= ‘quarantine’: emails will end up in the junk(spam) folder of the receiver
Conclusion of Email Spoofing
Spoofed mail is hard to detect for a person because mail looks legitimate.
To safeguard your domain and organization from email spoofing attacks implement SPF, DKIM, and DMARC records on your email server, and for email security best practices follow this blog.
In case of any help or query, please contact us or raise a ticket.


1 comments