When you first start using AWS, keeping track of what you have done is quite simple.
But, as your account profile expands, sub-optimal scenarios in terms of cost management and performance may emerge that go unreported.
In short, Unused AWS snapshots, storage volumes that are no longer in use, resources that are not tied to AWS EC2 instances, and the list goes on, all of which are costing your company money.
It’s also possible that you’ve set up resources that aren’t optimized for security, performance, or fault tolerance.
AWS Trusted Advisor is a service that examines all of the resources in your AWS account and recommends changes to bring them into compliance with AWS best practices.
What is AWS Trusted Advisor?
AWS Trusted Advisor is a real-time AWS tool that assists you in provisioning your resources according to AWS best practices.
It performs checks to assist you in optimizing your AWS infrastructure, improving security and performance, lowering overall costs, and monitoring service restrictions.
Always take advantage of the recommendations given by the Trusted Advisor, whether you wish to develop applications or as part of ongoing improvement.
Therefore, It helps maintain your solutions provisioned optimally.
There are 3 categories of fundamental recommendations c:
- No problem detected – a green check
- The investigation recommended – an orange exclamation mark
- Action recommended – a red exclamation mark
AWS Trusted Advisor Checks and Benefits
Trusted Advisor has a huge number of checks that can be performed on a variety of services. So, there are five different types of checks –
Cost Optimization
By identifying idle resources or committing reserved resources, recommendations made by Trusted advisors can help you save money.
- EC2
- Checks for any EC2 instances that consumed less than 10% CPU capacity or had network I/O < 5MB in the previous 14 days.
- Finds reserved EC2 instances that are about to expire in the next 30 days.
- Then it compares the use of reserved instances vs on-demand instances.
- EBS – Examines AWS volume settings and alerts you to any volumes that look to be underutilized.
- Load Balancers – Look for load balancers that aren’t in use.
- RDS –
- Look for database instances that don’t seem to be in use.
- Recommends utilizing RDS reserved instances instead of on-demand RDS where possible.
- Elastic IP – Looks for EIPs that aren’t linked to any EC2 instances.
- Route 53 – Looks for record sets that have been configured inefficiently.
- Redshift –
- Look for unused clusters in your Amazon Redshift architecture.
- Recommends using reserved nodes instead of on-demand redshift resources to save money.

Performance
By verifying your service limitations and monitoring instances, you can improve the overall performance of your applications and cloud infrastructure.
- EC2 –
- Checks for EC2 instances that have used 90% of their CPU for 4 days in the last 14 days.
- Check for an excessive number of rules in all of your security groups.
- EBS –
- Checks EBS magnetic volumes that are overused and could benefit from a more efficient design.
- Checks for volumes that may be impacted by the EC2 instance’s throughput capability.
- Route 53 – Looks for resource record sets that can be aliased.
- CloudFront –
- Examines the HTTP request headers
- Look for buckets on S3 that don’t use AWS CloudFront.
- Checks for CNAMES that have DNS settings that are wrongly set up.

Security
Users can harden their AWS services against intruders by setting various security mechanisms with the help of AWS Trusted Advisor.
- Security Groups –
- Checks security groups that provide unlimited access to specified resources.
- Examines the level of database access provided by security groups.
- IAM –
- To discourage the usage of root access, it checks for the presence of at least one IAM user.
- Check your root account for multi-factor authentication and issue a warning if it isn’t enabled.
- Check if the password policy for your AWS account is enabled, as well as the password content criteria.
- Active IAM access keys that haven’t been rotated in the last 90 days are checked.
- S3 – Examine your S3 buckets for open permissions or buckets that anyone with an AWS account may access.
- Cloud trail – This check verifies that you are using CloudTrail.
- Route 53 – looks for a valid SPF record in the record sets.
- ELB –
- Checks for elastic load balancers with listeners that do not communicate in an encrypted manner.
- Checks for security groups that aren’t related to the ELB, as well as configurations that allow port access that isn’t associated with the ELB.
- CloudFront –
- Check for issues with CF alternative domain names, as well as when they are about to expire.
- Check for SSL certificates that have expired, are about to expire, or are not encrypted properly.
- Access Keys – Checks for publicly exposed access keys in prominent code repositories, as well as suspicious activity on EC2 instances that could be the result of hacked access keys.
- Snapshots –
- Check the permissions of your EBS volume snapshots and issue a warning if they are set to public.
- Checks for and cautions about public Amazon RDS Database snapshots.

Fault Tolerance
Tips for improving the resiliency of your applications by identifying health issues, missing backups, and redundancy gaps.
- EC2 – Examines the distribution of EC2 instances throughout a region’s availability zones.
- EBS – Checking the age of your EBS volume snapshots.
- Load Balancer – Examine your load balancers for optimization.
- VPN Tunnel – Check how many tunnels your VPNs have configured.
- Auto Scaling Group –
- Checks for resource availability in the autoscaling group launch setup.
- Also examines the autoscaling groups’ health check configuration.
- RDS –
- Checking RDS instances for automated backups.
- When DB instances are configured in a single availability zone, it raises an alert.
- S3 –
- Check the S3 bucket’s logging configuration.
- And also Checks for versioning that has been suspended or disabled in S3 buckets.
- Route 53 –
- Check the setup of the Route 53 name server.
- Checks for resource record sets connected with health checks that have been destroyed.
- Also, Look for failover resource record sets that aren’t configured correctly.
- ELB –
- Checking for cross-zone load balancing.
- Also, checks for load balancers with connection draining turned off.
- Aurora DB – Checking any Aurora DB cluster with both public and private instances.

Service Limit
The service limit looks for resource usage that is more than 80% of the configured limitations. The following are the things it checks:
- DyamoDB
- EBS
- EC2
- Kinesis
- RDS
- Route 53
- SES
- VPC
- ASG
- CloudFormation
- ELB
- IAM

Features of AWS Trusted Advisor
You may further customize recommendations and monitor your AWS resources with AWS Trusted Advisor’s various features –
Recent Changes
On the console dashboard, you may keep track of recent changes in check status. Therefore, the most recent modifications are displayed at the top of the list to draw your attention to them.
Note – However, this feature is only available with a Business or Enterprise level support plan.
Exclude Items
You can modify the Trusted Advisor report by using the “exclude items” option (previously known as “suppress”). If items are not relevant, then you can exclude them from the check result.
However, The excluded items will appear individually, and you can restore (include) them at any time.
Action LinksBeta
On the console dashboard, you may view recent changes in check status. In order to draw your attention to the most recent changes, they are shown at the top of the list.
Access Management
You can restrict access to individual checks or check categories using Amazon Identity and Access Management (IAM).
Refresh
A check can be refreshed every 5 minutes. By pressing the Refresh All button in the top-right corner of the summary dashboard, you can refresh specific checks or all of them at once.
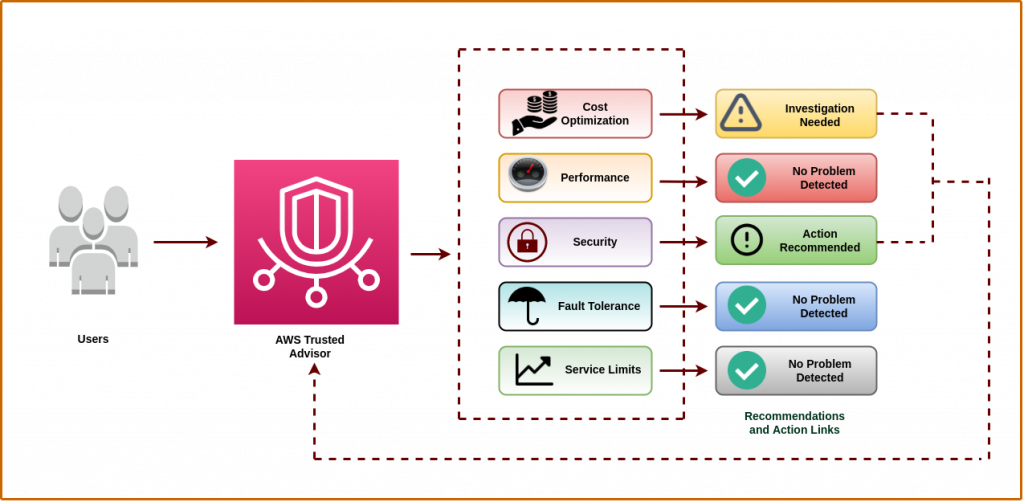
How does it work?
As shown in the image, each service category delivers appropriate checks that compare the organization’s architecture to AWS best practices.
Following the completion of the checks, the console presents an overview of the check, including the status and action recommendation.
Therefore, the action recommended section includes links to the services in the AWS Management Console, where administrators can take corrective action based on the recommendations.
A full dashboard is also available on the Trusted Advisor webpage, indicating the overall condition of each category.
Conclusion
As a result, It enables large organizations to consolidate expense suggestions from AWS Trusted Advisor across various accounts into a single spot.
Resource tags will also help to improve the data visualization and link cost opportunities to specific resources. Finally, the historical view of cost optimizations through time is a useful feature.
You may also visit our Magento development services and quality Magento 2 Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.