Traditional IT network security assumes that everyone and everything on the network is trustworthy. Outside access is difficult to get in typical IT network security, but everyone inside the network is assumed to be trustworthy.
The problem with this technique is that once an attacker has access to the network, they have complete control over it.
Today, information is increasingly distributed among cloud vendors, making it more difficult to establish a single security control for a complete network.
No one and nothing is trusted in a Zero Trust architecture.
What is Zero Trust Security?
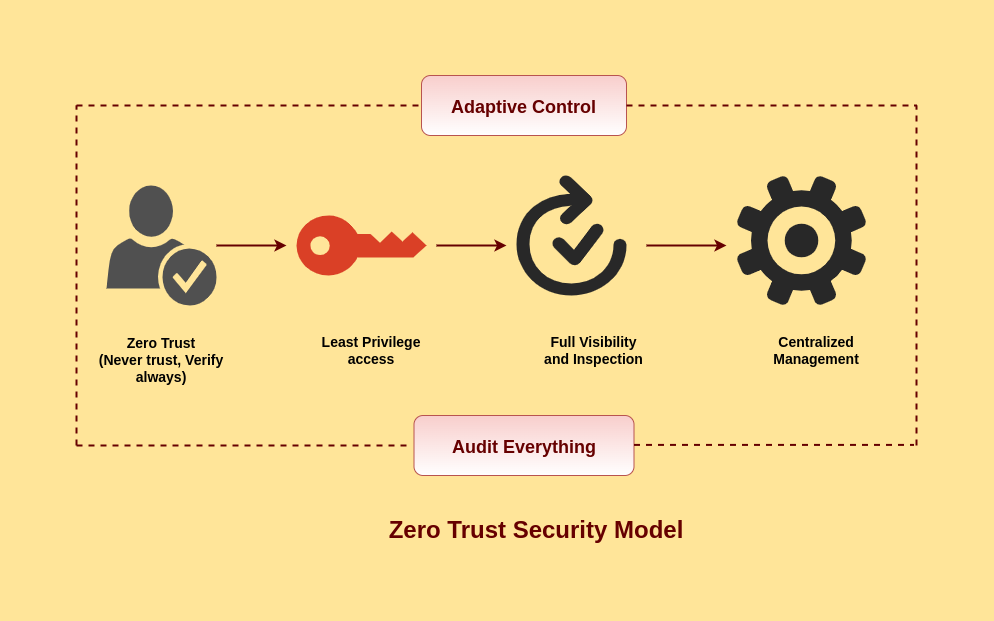
Zero Trust follows – the “never trust, always verify” principle.
Zero Trust is a network security concept based on the idea that no one or device, inside or outside an organization’s network, should be allowed to connect to IT systems or services until they have been authenticated and continually verified.
This additional layer of security helps to prevent data breaches. However, it assumes that there is no traditional network edge; networks can be local, cloud-based, or a mix of the two, with resources and workers located anywhere.
Zero Trust Security Principles
The Zero Trust model is based on the following principles –
- It must keep track of how many different devices are attempting to connect to its network, verify that each one is authorized, and examine all devices to guarantee they are not compromised.
- MFA, which requires more than one piece of evidence to authenticate a user, is also a basic value of Zero Trust security; simply typing a password is not enough to gain access.
- User identification and privileges and device identity and security are all verified by Zero Trust. Once established, logins and connections time out, requiring re-verification of users and devices on a regular basis.
- Providing users with only the level of access they require. This reduces each user’s exposure to network critical areas.
- It also employs micro-segmentation, which is the practice of dividing security perimeters into small zones in order to preserve separate access for different network segments.
Benefits of Zero Trust Security
Certain benefits of using Zero trust security are –
- Employees and partners will have secure application access.
- It assists in maintaining network trust and preventing harmful attacks.
- Reduces complexity and IT costs.
- Using identity, posture, and context-based rules to secure apps.
- Stop phishing and malware attacks before they happen.
How does it work?
By default, this security approach assures that data and resources are unreachable. Users can only have limited access to them under certain conditions, known as least privilege access.
A zero-trust security architecture verifies and authorizes every connection, such as when a user connects to an application or software to a data set via an application programming interface (API).
Further, It guarantees that the interaction complies with the organization’s security policy’ conditional requirements.
This strategy also uses context from as many data sources as possible to verify and approve every device, network activity, and connection based on dynamic policies.
This architecture necessitates a well-thought-out strategy and roadmap for implementing and integrating security measures in order to achieve certain business goals.
Zero Trust Network Access(ZTNA)
The main technology that enables enterprises to adopt Zero Trust security is Zero Trust Network Access (ZTNA).
It is based on established access control policies, which block access by default and only allow users access to services when they explicitly request it.
After authenticating a user through a secure, encrypted tunnel, ZTNA establishes secure access, allowing users to see just the apps and services that they have the authorization to see.
This defense approach eliminates lateral attacker movement, a vulnerability that cybercriminals use to scan and pivot to other services.
Organizations can use ZTNA to set up location and device-specific access control policies, preventing potentially hacked devices from connecting to their services.
Conclusion
In today’s modern digital transformation, Zero Trust is a framework for securing infrastructure and data. In addition, it solves the modern business concerns of securing remote workers, hybrid cloud systems; ransomware threats in a new way.
For Magento 2 Elastic search, please follow –
Our Cloudkul Blogs
Elasticsearch, Fluentd, and Kibana (EFK)
Setting up Elasticsearch, Logstash, and Kibana for centralized logging
Managing and Monitoring Magento 2 logs with Kibana
Our store modules –
You may also visit our Magento development services and quality Magento 2 Extensions.
For further help or query, please contact us or raise a ticket.