Transfer of messages in a secret way to protect data to the authenticated person has always been a subject of concern for decades.
From the use of pigeons to deliver messages on one click instant transfer, humans have solved the problem of communication.
But concerns like privacy and integrity of messages are always present in this zero-trust digital era.
Let’s explore key cryptographic concepts—encoding, hashing, encryption, obfuscation, and tokenization—for secure internet communication.
What is Cryptography?
Cryptography is a vital tool for safeguarding data sent over the internet.
It is the creative transformation of data into an unreadable format, only the intended recipient will be able to understand and use it.
As a result, cryptography is primarily concerned with securing and protecting data from cyber thieves or anybody other than the intended recipient.
Therefore, Cryptography allows people to communicate safely over the Internet.
However, to learn about the Role of Cryptography in Information Security, you can refer to the Blog.
The different cryptographic methods are –
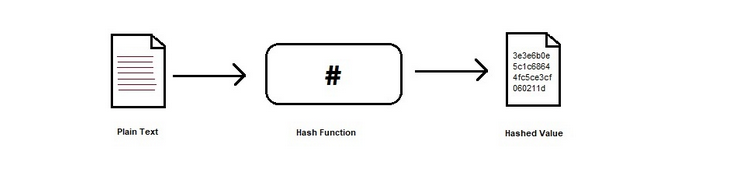
What is hashing?
It’s a cryptographic method that converts text into a fixed-length, irreversible string called a hash value or digest.
A single bit of change in the original text can bring an avalanche effect to the hashed string and will result in a different hash.
A good hash function should be complex and should not reproduce the same hash value for two different inputs.
We use hashing to ensure the integrity of the message.
For example: many stores provide software along with their hash value so that users can ensure the integrity by calculating the hash value of downloaded/purchased software on their own.
Hash functions are also used to avoid duplicity of data, to avoid storing clear text passwords database administrators use functions to store passwords in hashed value.
Some widely used Hash cryptographic algorithms are – MD5(Message digest) and SHA-2( Secure Hash Algorithm).
What is Encoding?
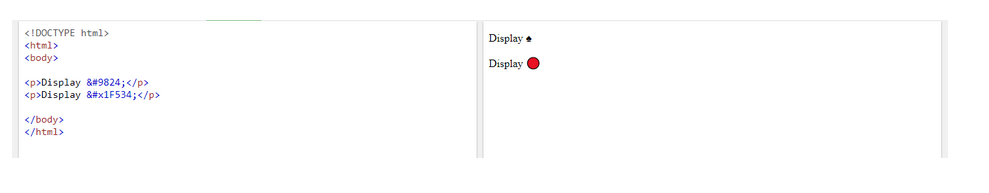
Mapping a character with another to make it understandable by that application or machine.
Here encoding is used to ensure that the application can understand the delivered string and be able to process it, rather than keeping the information secure.
Encoded strings can be decoded using the same scheme that is used to encode, a key is not required for both the processes.
The above snippet shows an example where a text(“♠”) is converted into a spade and another text(“🔴”) into a big red circle using utf-8 encoding scheme.
Other encoding schemes: Base64, ASCII, URL Encoding, etc
What is Encryption?
Encryption is the process of taking a message and scrambling its content so that only authorized people can access it.
Encryption service protects sensitive data, both online (bank details, emails, social networks) and offline (stored on hard drives), ensuring only authorized access.
By using encryption techniques we can enhance our security by preventing attacks like identity theft, and eavesdropping and can maintain confidentiality throughout the communication.
Although there are many encryption systems, the most common ones are the use of public and private keys.
Let’s talk about the types of encryption:
1. Symmetric key encryption:
This technique of encryption involves only one secret key to encrypt and decrypt the information.
Both sender and recipient must know the secret key, making symmetric encryption faster, but it requires secure key storage and a safe channel for key transfer.
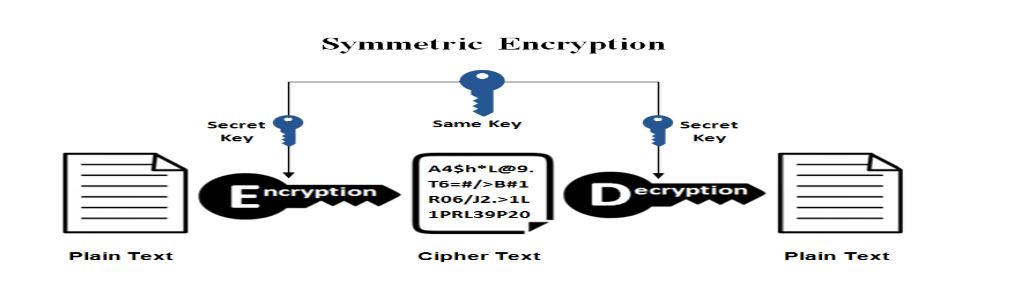
Some widely used Symmetric cryptographic algorithms are – AES-128, AES-256, DES-3, and BLOWFISH.
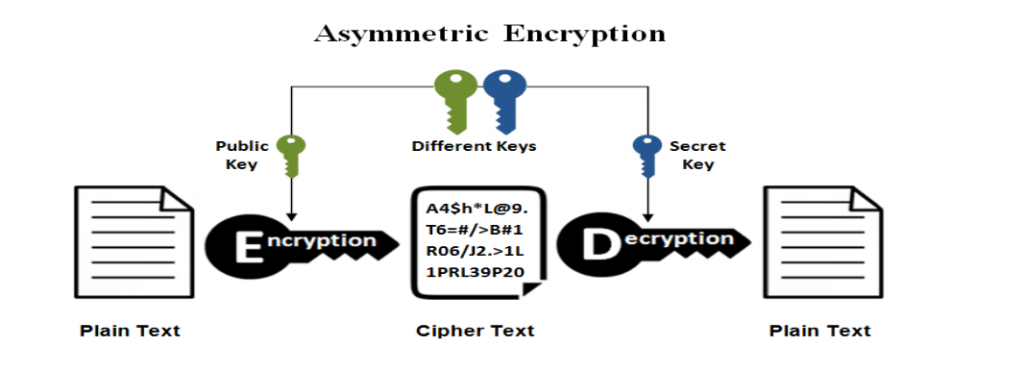
2. Asymmetric key encryption:
This technique uses two keys: a private key and a public key, where the private key will be a secret key and the public key will be a public key.
For instance: you share your public key with the public so that anyone who wants to send you a message can encrypt the message using your public key and send it to you.
Now as only you have access to your private key, only you can decrypt the message.
Some widely used Asymmetric cryptographic algorithms are – RSA, DSA, Elliptic curve techniques, and PKCS.
What is Obfuscation?
Obfuscation is the practice of making something difficult to read and understand.
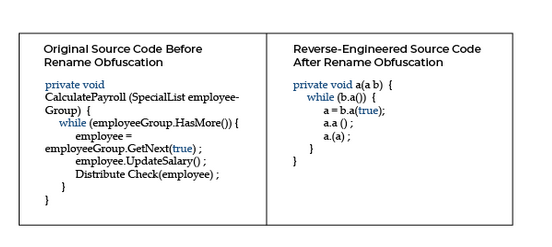
Generally, software’s code is obfuscated to protect developers/company intellectual property from being copied, to avoid tempering, and to defend code from attackers.
How it works:
It may involve the encryption of code, stripping out potentially revealing metadata, renaming important class names, and variables, and adding null bytes, and meaningless code.
Some other techniques like the use of Packers, crypters, or Exclusive or Operation are common practices.
What is Tokenization?
Tokenization is a way of protecting sensitive information by replacing it with an algorithmically generated secure random token.
Tokenization replaces sensitive cardholder details with a token to avoid leaking banking sensitive information over the internet during transactions.
Tokenized data is irreversible and can not be predictable, as there is no relationship between the token and the original data.
Therefore, even if information is leaked, attackers will not be able to use it.
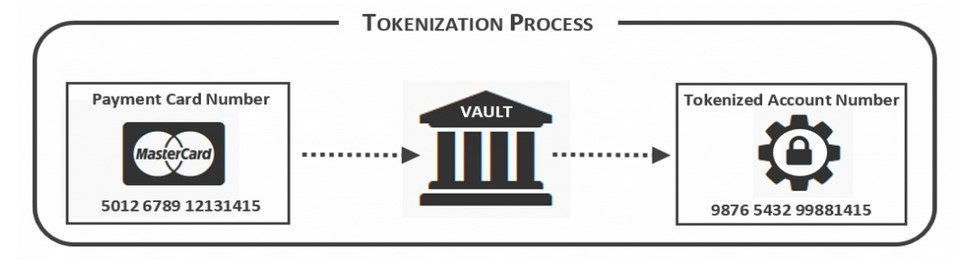
We can achieve Detokenization through the original tokenization system. There is no way to obtain original data from just a token.
So far we have discussed different techniques and where to use them to achieve our goal of secure communication over the Internet.
To improve the security of your e-commerce store check out the Webkul basic security module which is customizable and Magento 2 based eCommerce store security extension.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/.
You may also visit our Odoo development services and quality Odoo Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.