Many of us connect in cyberspace without giving security a second thought in today’s rapidly growing digital communication and electronic data exchange.
On the internet, we share a large amount of our personal information and secrets. Our digital footprint is in cyberspace whether we want it or not.
To be more specific, whatever we send is usually unprotected and vulnerable to cyber criminals.
As a result, current cryptography is in high demand to identify new ways to protect sensitive or confidential data.
Effective data encryption and decryption are the keys to cyberspace security.
As a result, we must convert information into an unreadable format, which can be protected and accessible only by those who are permitted.
What is Cryptography?
Cryptography is a tool for safeguarding data sent over the internet. It is the transformation of data into an unreadable format, only the intended recipient will be able to understand and use it.
As a result, cryptography is primarily concerned with securing and protecting data from cyber thieves or anybody other than the intended recipient.
Therefore, Cryptography allows people to communicate safely over the Internet.
As a result, cryptography enables customers to conduct online shopping using public or private media, such as the Internet, while avoiding thieves and password sniffers.
We can achieve it by utilizing the most recent computer science technological improvements.
Cryptography, usually referred to as cryptology, is a branch of mathematics that deals with the encryption of data.
Encryption and decryption keys are key aspects to start cryptography –
Encryption – Encryption is the process of coding and transforming plain text into an unreadable format.
Decryption – Decryption is the process of decoding and converting unreadable material into readable information using a particular digital key.
Elements of Cryptography
The cryptographic layers are safe because of their core elements –
Cryptographic Key
To safeguard sensitive information, cryptographic keys will be used in conjunction with cryptographic algorithms.
To be effective, cryptographic keys must have an adequate key length and private keys must be kept secret.
Cryptographic Algorithm
These algorithms are the mathematical prerequisites that ensure the integrity, confidentiality, and validity of sensitive data.
Cryptographic Libraries
Cryptographic Libraries are libraries that contain implementations of cryptographic algorithms that application developers can utilize to safeguard sensitive data.
To provide the desired security level, cryptographic libraries must be carefully chosen and kept up to date.
Digital Certificates
Digital certificates are used to establish confidence between digital components that are linked together.
To eliminate security vulnerabilities, digital certificates must be handled effectively to guarantee that compliance algorithms and key lengths are used, as well as being renewed before expiration.
Types of Cryptography
There are 3 types of Cryptography –
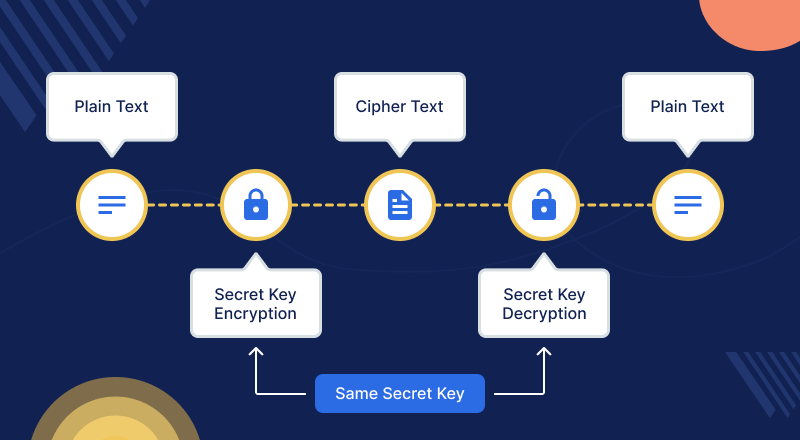
Symmetric Encryption or Secret Key Cryptography
In this method, only one digital key will be used. Encryption and decryption are done with the same digital key.
When the original data sender encrypts the data into an unreadable format, he uses the same key, and the recipient uses the same key to decrypt the data into a readable format.
This is a straightforward method of cryptography with one major flaw. The sharing of a single key could lead to misuse.
The Data Encryption Standard(DES) is the most popular example of a symmetric–key system.
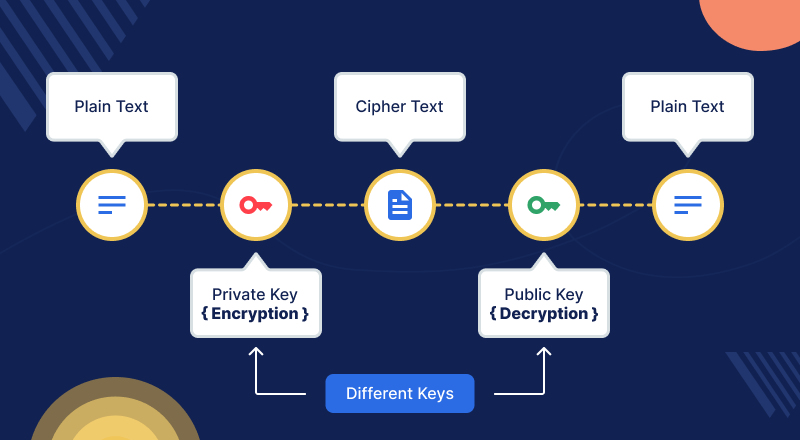
Asymmetric Encryption or Public-key Cryptography
Each communication party has a set of keys in this type of encryption. One key is private, while the other is open to the public. They all have access to the same public key.
When delivering information, the sender encrypts it with the public key. When the recipient receives the encrypted data, he uses his secret key to decrypt it into a readable format.
The most extensively used type of public-key encryption is RSA.
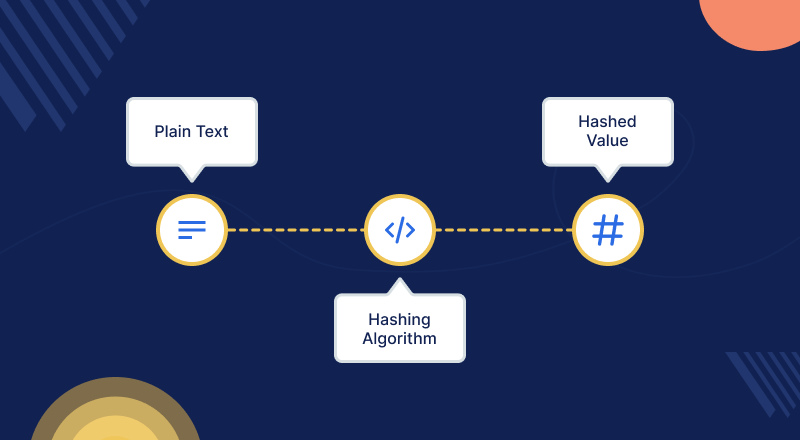
Hash Function
It uses a set length hash value encrypted into plain text, this method of encryption does not require any digital keys.
The hash key’s function is to ensure that the original data is not tampered with.
It facilitates communication through the use of algorithms. The hash key creates a digital fingerprint of the file, ensuring it is neither corrupted nor compromised with a virus.
This encryption is one-way. Computer administrators can also use the hash key to encrypt passwords.
Role of Cryptography
Cryptography achieves confidentiality, integrity, authentication, and non-repudiation, among several other information security goals –
It protects the confidentiality of the information
Confidentiality means that only those with the appropriate permissions can access the data sent and that this data is safeguarded from unauthorized access at all stages of its lifecycle.
The only way to keep data secure while it’s being kept and delivered is to encrypt it.
Without the correct decryption keys, even if the transferor storage medium is hacked, the encrypted data is largely useless to unauthorized parties.
It ensures the Data Integrity
The accuracy of information management and associated information is what integrity means in the security context.
When a system is referred to as ‘integrated,’ it means that data is delivered and processed in a controlled manner. Even after it has been processed, the data remains the same.
To maintain data integrity, encryption employs hash function algorithms and message digests.
It assures the Authenticity of the sender or receiver
Identifying the source of information is a key principle of cryptography. It is simple to communicate securely once the source of information is recognized.
Authentication is only possible if the sender provides a unique key exchange that can be used to authenticate his or her identity.
A login and password are generally used, although additional techniques such as a smart card, retina scan, voice recognition, or fingerprint scan can also be used.
Non-Repudiation
This approach ensures that the sender of the information cannot claim that it was never sent. This method employs digital signatures to prevent the sender from denying the data’s origin.
It also ensures the Availability of Data
Cryptography also contributes to data availability by ensuring that only individuals with the proper rights can access networks and retrieve data in a reliable and timely manner.
Conclusion
So, Cryptography is a dynamic and necessary part of digital commerce.
It is being used by businesses of all sizes and across industries to secure personal information, customer data, trade secrets, employee files, credit card numbers, and other sensitive data.
Encryption protects your company’s data and information from potential risks, ensuring that even if an intruder obtained access to your sensitive data, they’d be unlikely to be able to read any of it.
However, If you are looking for a security audit service, check out the Webkul basic security module.
Check out this Magento 2-based eCommerce store security extension which can also be customized.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/.
You may also visit our Odoo development services and quality Odoo Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.