In today’s world, security is the most worrying factor. Due to lack of security, there is always a risk of losing sensitive information. Therefore, we need to protect our infrastructure to the fullest extent possible, to protect ourselves from cyber attacks of all forms, and to protect our confidential data from unauthorize access and information exfiltration. In addition, there are three key principles that requires to secure information, and these principles are known as CIA Triad. Likewise, these principles are also known as the safety analysis model.
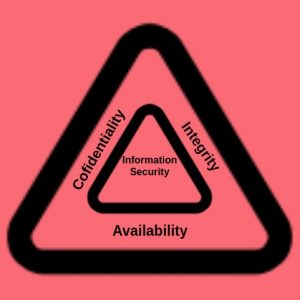
CIA Triad
CIA Stands for Confidentiality, Integrity and Availability. It’s an online balancing information system. The CIA triad is therefore a model that describes the three key objectives requires to achieve information security. And if any of them breaches, then it can have significant repercussions for the involved parties. It is a security model that provides key data protection and serves as a guide for organizations to protect their confidential data from unauthorize access and information exfiltration.
Breakout of CIA Model
Confidentiality, integrity and availability, these are the most basic concepts for protection of the information. Such, principles must always be part of the core goals of information security activities in the CIA triad. Therefore, the CIA Triad is an acronym for:
CIA : Confidentiality
Confidentiality is the protection against unauthorize access to the information. It simply defines as keeping information secret or hide from unauthorize peoples. Therefore, it ensures that access to the information is grant only to authorize persons.
Conditions which breaks down Confidentiality
- Laptop burglary – When a laptop has been stolen, destroy or lost due to certain circumstances.
- Password theft – It just means stealing passwords from other network users.
- Sensitive emails sent to the unauthorize peoples.
Methods that ensure Confidentiality
- Cryptography
- ACL (Access Control List).
- By using Usernames and passwords.
CIA : Integrity
Integrity defines the state in which the information is kept correct and consistent until the allowable changes are permit. In brief, it ensures that the data are accurate and complete. Therefore, it simply means maintaining the data or information in its actual state without any alteration. And if changes requires, then only authorize persons should do so.
Conditions which breaks down Integrity
- Security Attacks – security attacks are unauthorize acts to destroy, alter or steal sensitive data against private, corporate or governmental IT properties.
- Software Exploits – It refers to the software or operating system’s failure, malfunction, or bugs.
- Crashing of Server – If the web server software behind a website crashes, the situation is known as a server crash.
Methods that ensure Integrity
- Encryption.
- Hashing.
CIA : Availability
Availability describes the situation in which information is available when and where it is rightly requires. It simply means the information or data available as and when requires. Basically, it’s main objective is to provide the information upon access by authorize users.
Conditions which breaks down Availability
- DoS (Denial of services) – It is an attack that attempts to shut down a system or network, which makes it impossible for its intend users to access it.
- Breaking of website or server – If the web server software behind a website crashes, the situation is known as a server crash or breaking of website.
Methods that ensure Availability
- Maintenance of hardware.
- Prevention against DoS/DDoS.
Non Repudiation
Non-repudiation means the ability to meet contractual obligations. Meanwhile, the sender or receiver cannot decline a transaction. Therefore, it refers to a service that provides evidence of the data sources and the data integrity. It can usually be done through the use of Digital Signatures. To know more, visit.
Digital Signature
Digital signatures are often use to fulfill three main information security goals: integrity, authentication, and non-repudiation. It use a standard accepted format to offer the highest security and universal acceptance. Therefore, this is a method that verifies the authenticity and integrity of a file, message, software or digital document by using public and private keys. For further reading, just click.
Conclusion
In short, the CIA security triangle is an important security principle. As it incorporates all security controls, procedures, and protections. Moreover, the CIA triad has confidentiality, integrity and availability priorities which are fundamental factors in information security. As a result, organizations need to preserve the authenticity of their information. Which means balancing confidentiality, Integrity and availability: the CIA Triad.
In case of any help or query, please contact us or raise a ticket.


Be the first to comment.