One of the most crucial riddles to answer for a fully effective defensive strategy is determining who is behind an attack.
Whether the company is being under target or is just a victim of a widespread computer network attack can have a significant impact on how they respond and allocate resources.
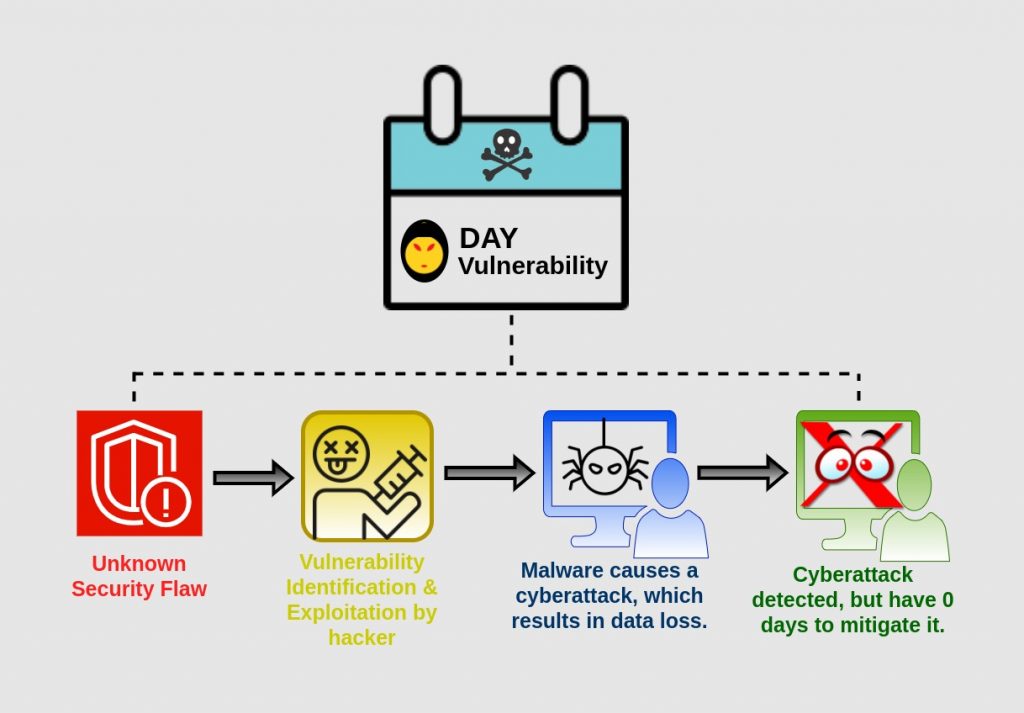
In the realm of information technology, the term “zero-day” is derogatory. In recent years, zero-day vulnerability attacks have become one of the most serious cyber threats.
“Zero-Day” Vulnerability Attack
The term “zero-day” refers to a vulnerability or attack vector that only attackers are aware of, allowing it to run undetected by defenders. It is also known as zero-day exploits.
These are the flaws in the software, firmware, hardware, operating systems, or computer network that security companies are unaware of. As a result, no ready-to-use patch exists.
The term ‘zero’ refers to how long the security provider has known about the flaw but has yet to discover a solution.
Hackers, however, take advantage of this limited window of opportunity to develop lethal malware and exploit system security holes.
Consequences of Zero-day Vulnerability Attacks
Revenue Loss
Massive financial losses can occur if the systems are unavailable for even a few hours as a result of the attack.
The large sums of money spent on investigations, response activities, and recovery measures in the aftermath of the attacks also result in losses.
Legal Repercussions
When such hacks occur, it is necessary to show that security carelessness was not implicated to regulatory authorities.
Otherwise, have to face legal action and be required to pay substantial fines and penalties if it is proven otherwise.
Reputational Damage
If the attack becomes public, the brand’s reputation will suffer significantly.
It conveys a message to the public that cybersecurity procedures are insufficient, making data and systems especially vulnerable to attack.
Loss/theft of data
Attackers can use a zero-day vulnerability to steal vital and sensitive data from the company, its employees, and customers.
They could steal money, sell the information on the dark web to other hackers, commit identity theft, or extort the victims using the information.
Decrease in production
Manufacturing equipment, electronic communication networks, and other systems are vulnerable to the exploit. Production, as well as individual and organizational productivity, has come to a halt.
Unauthorized access
Hackers can take advantage of the flaw to get unauthorized access. They might use phishing or malware to send malicious messages to the contact list.
Prevention
Protection, detection, and response are three essential preventative measures. Some related suggestions are:
- Update your software and systems with the newest anti-virus and security patches.
- Always use the latest version of browsers.
- Perform code audits, manual testing, and automatic testing regularly to guarantee that security is flawless.
- Prepare an all-encompassing cybersecurity disaster recovery plan.
- Employees need training to understand typical security threats, as well as how to avoid and respond efficiently in the event of an incident.
- Always use Secure Sockets Layer (SSL) encrypted websites.
- Install multi-layer security technologies, such as Web Application Firewalls, and conduct daily scans for abnormalities and suspicious activity.
Conclusion
As a result of the rapid digital transformation, the number of 0-day vulnerability attacks is expected to increase.
No one can forecast them or guarantee that they will be resolved quickly when they occur.
As a result, the only way to cope with them is to lessen the frequency and severity of their occurrences.
If you are looking for a security audit that identifies vulnerabilities like cross-site scripting, guessable credentials, and other misconfigurations, check out the Webkul basic security module.
Check out this Magento 2-based eCommerce store security extension which can also be customized.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/.
You may also visit our Odoo development services and quality Odoo Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.