E-commerce-based stores are increasingly being compromised, and web protection needs to be at the top of the list.
Being protected in the online world is becoming more and more important every day, and it is vital to protect your website and the data it holds.
If your store is not secure, then unauthorized people would be able to use your store to infect your site’s visitors with malware and steal your customer’s data.
The truth is that a customer loses confidence because of a compromised store and it can lead to a loss of the company’s credibility, which can also mean an end to the business of e-commerce.
So, let’s discuss the risk of Broken Authentication and Broken Access Control – The most popular web application threats today.
OWASP is a not-for-profit organization that protects against web application threats or risks. They also released the OWASP Top 10 which describes the major threats to web applications in detail.
Broken authentication and broken access control on OWASP’s top 10 vulnerabilities in 2017 are ranked 2nd and 5th.
And in 2023 list Broken access control and broken Authentication (known as Identification And Authentication Failures) are ranked 1st and 7th.
Broken Authentication

Authentication means the validation or authentication of credentials, such as username/user ID and password for identity verification.
Whereas, Broken authentication refers to an act enabling unauthorized persons to steal login data from a user or forge session data, such as cookies, to gain unauthorized access to websites.
Vulnerability in Authentication helps unauthorized persons intercept the authentication methods that a web application uses.
The effect would be serious because the unauthorized persons log into the account as authorized users.
How does it break?
- Insufficient password policy.
- Submit credentials over an unprotected channel.
- Insecure system for accessing passwords.
- Leakage of details while logging in failed.
- Unlimited log-in attempts.
Outcomes of Broken Authentication
- Damage to confidentiality.
- Provides complete access to the unauthorized user.
- Account theft, confidential data may be stolen from authorized users.
- Damage to reputation and business loss.
Prevention
- Where possible, enforce multi-factor authentication(2 FA) to prevent attacks.
- Align the length of the password, complexity, and rotation policies with NIST 800-63 B’s guidelines in section 5.1.1.
- Limits failed log-in attempts. Monitor all flaws and warn administrators when detecting credential stuffing, brute force, or other attacks.
- Use a server-side, stable, built-in session manager that generates a new, high entropy random session ID after logging in. After logout, idle, and total timeouts, session IDs should not be in the URL, safely saved and invalidated.
Broken Access Control
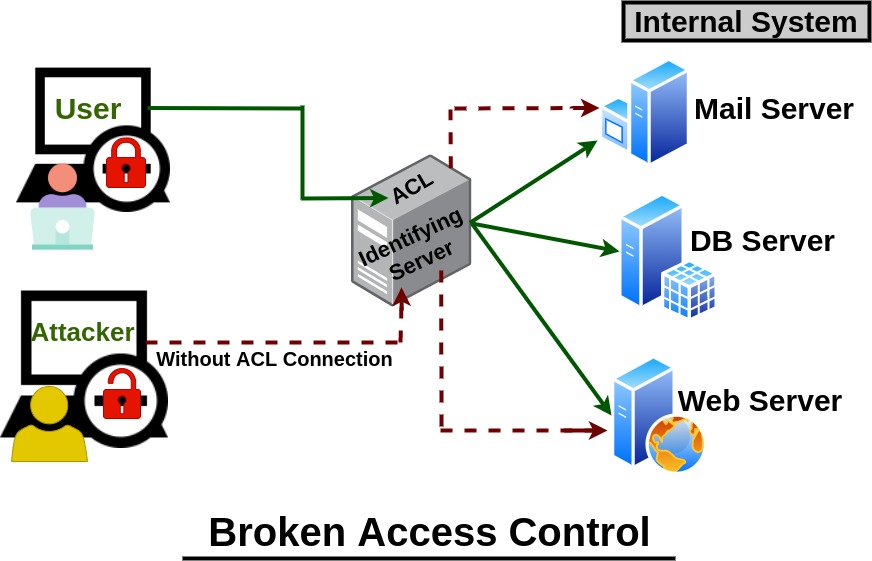
Access control is a method of determining the rights/privileges of access to data and functions, or deciding whether an authenticated individual has access to the specific data or not.
It simply outlines the permissions of an authenticated person to access data. It refers to a collection of policies that limit access to data, devices, and physical locations.
If unauthorized users can view or alter content, perform unauthorized actions, or take control of the site, it’s called Broken Access Control
How does it break?
- Intercepting authentication of access control by altering the URL, HTML page, and internal application state.
- Not limiting others to accessing or changing the record or account of someone else.
- Escalation of privilege – Acting as an admin user while signing in as an unauthorized user.
- Tampering or replaying metadata to elevate rights.
- Misconfiguration with CORS (Cross-Origin Resource Sharing) that enables unauthorized access to the API.
Prevention
- Explicitly test and document the access control specifications for each application service. And regularly check the server/application to identify the flaws in the access controls.
- Verify each single request. And use programmatic techniques to ensure that no exceptions will occur.
- Avoiding forced surfing by only granting users access rights equal to their privileges.
- Add additional access restriction with IP address for more sensitive functionalities.
Conclusion
Nowadays, web application security is a high-ranking issue, Authentication and Control Access is just a slice of the entire pie but the consequences of such threats can be disastrous.
Faulty access controls can allow unauthorized users to take over the application, access admin features, and manipulate sensitive data.
Overall, a better way of avoiding these attacks is to implement effective Authentication and Access Controls for each privileged page in the application.
Besides that, looking for a security audit service? check out the Webkul basic security module.
Check out this Magento 2-based eCommerce store security extension which can also be customized.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/.
You may also visit our Odoo development services and quality Odoo Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.