So far in this Magento 2 security series, We have discussed injection, XSS, CSRF and CORS attacks and the effective way to secure Magento 2 store from them.
Let’s discuss another attack named as Header manipulation, Header manipulation is a type of attack in which a malicious actor insert malicious data, which has not been validated, into an HTTP Response header. This is also known as response splitting attack.
How HTTP header manipulation work
Header manipulation attack exploit application that allows CRLF (carriage return (\r) or line feed (\n)), as input which gives the attacker to control the header and body of the HTTP response (CRLF is one of the scenario for header manipulation attack). A majority of header manipulation attack occur due to the value of “location” header is not properly sanitized.
Attack Scenario
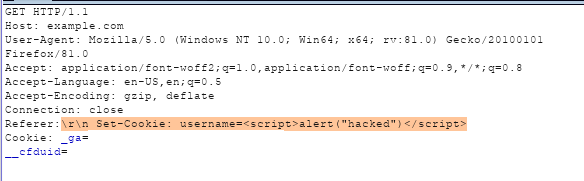
We have manipulated “referrer” header value, Which is reflected in the “location” HTTP response header.
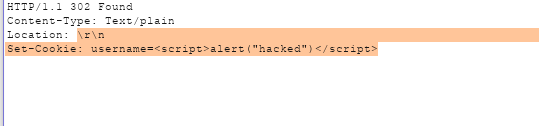
Because the “Location” header value is empty and \r\n break statement, the web browser will ignore that header and the rest of the headers will be parsed by the web browser. As a result, the attacker will be able to successfully execute a malicious header (“Set-Cookie”).
Impacts
- Open Redirection: By changing the value of location header, attacker can control the redirect URL and can redirect the user to malicious website.
- Cookie Manipulation: Using CRLF (\r, \n) an attacker may change, add or even overwrite a legitimate user’s cookies.
- Cross-Site Scripting: Once the attacker has control of the response, he can easily include malicious JavaScript into the HTTP response body.
- The impact of header manipulation attacks vary, and It can also deactivate certain security restrictions like XSS Filters and the Same Origin Policy in the victim’s browsers.
How to secure your magento2 store against Header manipulation attack
- The best way to secure magento2 store is to not use user’s input directly inside response headers, or always use a function to encode the CRLF special characters.
- Always use an updated version of your programming language that does not allow CR and LF to be injected inside functions that set HTTP headers.
Although it’s not possible for every store owner to check against header manipulation vulnerabilities in their store, in such conditions Webkul can help in detection and in mitigation from vulnerabilities on Magento 2 store through its basic security module which can also be customized.
To safeguard your Magento 2 store from other attacks like a malicious file upload or brute force, visit our store and check out our Security Extension Suite for Magento 2 module for more details, which is effective in blocking malicious users and in notifying admins for suspected login attempts.
In case of any help or query, please contact us or raise a ticket.