
The widespread availability of public cloud services like AWS has provided numerous benefits for companies.
Quick infrastructure setup, scaling with a few clicks, and delegating service management so you can focus on your product are just a few examples.
Working with a public cloud service, on the other hand, comes with its own set of issues, one of which is the difficulty of auditing your resources, which is where AWS Config comes in.
AWS Config
AWS Config is a service that lets users review, audit, and evaluate AWS resource configurations.
Config continually monitors and records AWS resource configurations, to allow users to compare recorded configurations against desired configurations in an automated manner.
Users can use Config to review configuration changes, track resource histories, and assess compliance with internal rules across AWS resources.
This makes compliance auditing, security analysis, change management, and operational troubleshooting much easier for users.
AWS Config Rules
AWS Config Rules allow you to specify desired configuration parameters for individual resources or the entire account.
It monitors resource configuration modifications against the rules and flags resources that are out of compliance.
There are 2 types of rules –
AWS Config Managed Rules
Config managed rules are pre-built and are administered by AWS. AWS takes care of maintaining and updating the rules for you, therefore, which is convenient.
In compliance with common best practices, you can customize managed rules.
Let’s discuss some of the predefined AWS Config Managed Rules –
iam-root-access-key-check
Checks for the availability of the root user’s access key. If the user access key does not exist, then the rule is COMPLIANT. NON-COMPLIANT otherwise.
Region not supported – Asia Pacific (Osaka)
root-account-mfa-enabled
Check if your AWS account’s root user requires multi-factor authentication for console sign-in.
Region not supported – China (Beijing), China (Ningxia), AWS GovCloud (US-East), AWS GovCloud (US-West) Region
access-keys-rotated
Check if the active access keys have been rotated within the specified maximum number of days. If the access keys have not been rotated for more than specified, then the rule is NON-COMPLIANT.
Region not supported – All Regions Supported
s3-bucket-public-read-prohibited
Check if public read access to your Amazon S3 buckets is disabled.
Regions not Supported – All Regions Supported
ec2-instance-no-public-ip
Checks Amazon EC2 instances are associated with a public IP address. If the public field is present in the Amazon EC2 instance configuration item, then the rule is NON-COMPLIANT.
However, This regulation only applies to IPv4 addresses.
Regions not supported – Asia Pacific (Osaka) Region
desired-instance-type
Check to see if your EC2 instances are of the specified class.
Regions not Supported – All Regions Supported
We’ve only covered a few of these rules, but there are plenty more that can help you protect your cloud resources. For further rules, please visit AWS Config Managed Rules.
AWS Config Custom Rules
AWS Lambda functions have custom rules that we can customize to match our needs. They prove to be useful when the managed rules aren’t quite up to the task.
This is where AWS Lambda and serverless technology come into play. You may establish your security and compliance posture and add your custom business logic.
AWS Config Benefits
- It is a service that provides AWS resource inventory, configuration history, and configuration change notifications to allow security and control.
- Secondly, It gives you a complete picture of how you are configuring your AWS resources in your account.
- It provides point-in-time and historical states, as well as the ability to graphically see changes in a timeline.
- When numerous configuration changes to a resource are performed in a short period, it will only store the most recent configuration of that resource; this represents the cumulative impact of the full series of changes.
- By comparing the latest functional configuration to the one that was recently updated and producing issues, AWS Config can assist in quickly detecting and troubleshooting issues.
- AWS Config aids in the discovery of resources within an account, resulting in improved inventory and asset management.
How does AWS Config Work?
- After enabling AWS Config, it first finds the account’s supported AWS resources and creates a configuration item for each of them.
- When the configuration of a resource changes, it generates configuration items, and it keeps historical records of the configuration items of the resources from the time the configuration recorder is started.
- It creates configuration items for all supported resources in the region by default, however this can be limited to specific resource types.
- By performing the Describe or List API calls for each resource as well as linked resources in the account, it keeps track of all changes to the resources.
- It additionally keeps track of modifications made to the settings that were not started by the API.
- It checks resource configurations regularly and generates configuration items for those that have changed.
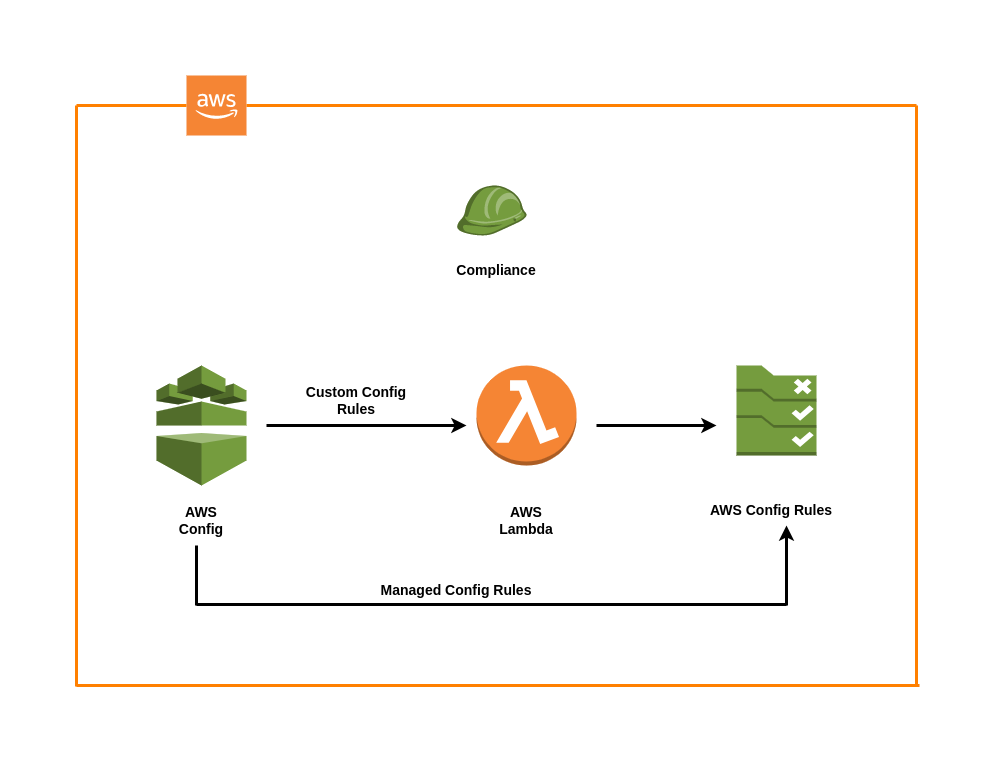
With Config Rules –
- For resource configurations for desired settings, config rules are assessed continuously.
- Secondly, Resources are reviewed in reaction to configuration changes or regularly, depending on the rule.
- When AWS Config assesses the resources, it calls the AWS Lambda function for the rule, which contains the rule’s evaluation logic.
- If a resource breaks a rule’s conditions, as a result, the resource and the rule will be noncompliant, and a notification will be delivered to the AWS SNS(Simple Notification Service) topic.
Example
Let’s understand the working of AWS Config using a use case example –
Let’s suppose we are running an ERP solution. After benchmarking our application under different scenarios, we concluded that t2.medium (i.e., 2 vCPU and 4 GB RAM) gives us desirable performance.
If we scale down the server, it may lead to degraded app performance and will affect the user experience also, server scale-up-related changes will unnecessarily add extra cost to the AWS billing.
In this case, we will use AWS Config to track our AWS resource configurations to compare our current configurations against desired configurations.
We can use custom rules with a Lambda function to enforce our server configuration benchmarks, ensuring configurations meet required standards.
After enabling the AWS config, it will audit our resources and will trigger the Lambda function if any change is found.
Lambda will implement the business logic and therefore, will check the configurations for what we had set and with what is desired.
In this way, AWS config helps organizations ensure that the desired configurations are maintained on critical resources/services.
Pricing
For every AWS Region, you pay $0.003 per configuration item stored in your AWS account. Every time a resource’s configuration or relationship changes, therefore, it creates a configuration item.
You will have to pay only for the number of AWS Config rules evaluations recorded, not for the number of active rules in your account per region.
| AWS Config rule evaluation | Price |
| First 100,000 rule evaluations | $0.001 per rule evaluation per region |
| Next 400,000 rule evaluations (100,001-500,000) | $0.0008 per rule evaluation per region |
| 500,001 and more rule evaluations | $0.0005 per rule evaluation per region |
Conclusion
AWS Config makes it simple to keep your cloud environment secure and compliant thanks to its preset rules that can be installed quickly and easily.
Hence, AWS Config is a powerful feature that every organization using Amazon’s cloud should consider.
In our next blog, we will further discuss how we can manage our Multiple accounts in AWS.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/.
You may also visit our Magento development services and quality Magento 2 Extensions.
For further help or queries, please contact us or raise a ticket.


Be the first to comment.