All versions of the Lite-speed Cache WordPress plugin, including 6.3.0.1, are susceptible to privilege escalation.
The reason for this is that the role simulation feature is not appropriately restricted by the plugin.
Lite-speed Cache is one of the most widely used caching plugins for WordPress, with over five million active installations.
Lite-speed Cache
This is a sophisticated caching plugin designed for WordPress that significantly improves website performance.
It achieves this by storing frequently accessed data in a cache and, as a result, reduces the need for repeated server processing and data retrieval.
As a result, this caching mechanism allows web pages to load more quickly for visitors, enhancing the overall user experience and reducing server load.
Lite-speed Cache for WordPress works by creating and storing temporary copies of each web page on your site.
However, these copies are saved on the local server where the Lite-speed software is installed, not on any external servers or accessed by Lite-speed employees.
Identifying Vulnerability
We recently heard about this plugin being in the news and looked into it on several platforms. However, we found out that the reports are true:
The plugin is vulnerable to an ‘unauthenticated privilege escalation‘ attack. After that, we decided to reproduce this vulnerability on our local system,
And found that the Lite-speed Cache plugin version 6.3.0.1 is indeed vulnerable to an ‘unauthenticated privilege escalation‘ attack
The Lite-speed Cache plugin for WordPress is vulnerable to privilege escalation in all versions up to and including 6.3.0.1.
This happens because the plugin doesn’t properly limit role simulation.
However, If an attacker can find a valid hash (from debug logs or by guessing), they can pretend to be an administrator and use the REST API endpoint to create a new admin account without being logged in
Understand The Security Flaw
The async_lite-speed_handler() function had a security flaw because it didn’t properly check who was allowed to use it.
This allowed anyone to trigger it and create a special $hash value that was stored in the database.
This hash could then potentially be used for malicious purposes if not handled securely.
Loose Comparison: A way of comparing values in programming where the comparison isn’t very strict.
It often allows different types of data (like numbers and strings) to be considered equal if they look similar.
Example:-
If (“123abc” == 123)
{
Echo “They are equal”
}
A security risk with loose comparison is that it allows values that aren’t exactly the same to be considered equal due to type conversion.
However, this can let an attacker use a slightly incorrect or manipulated value to bypass security checks, making the system vulnerable to attacks.
Capability Check: Normally, functions should check the user’s permissions (capabilities) to ensure that only authorized users (like administrators) can perform certain actions.
Nonce Check: A nonce is a security token that helps prevent certain types of attacks (like Cross-Site Request Forgery or CSRF). It also ensures that the request is coming from a trusted source.
Role Simulation Using Cookies:
Cookies Used: The function relies on two specific cookies:
lite-speed_role: This cookie presumably contains a role name (like “administrator” or “editor”).
lite-speed_hash: to match the value in the database.
Cookie Manipulation: If an attacker can manipulate their cookies, then they could set their lite-speed_role cookie to any role, including an administrative role, and can set the lite-speed_hash to match the value in the database.
No Additional Security Checks: Basically, the function only checks if the cookie values match what’s in the database.
However, It doesn’t check if the user is authorized to perform this action or if the cookie is coming from a legitimate source.
Privilege Escalation: By manipulating these cookies, an attacker could simulate being a higher-privileged user (like an administrator)
Gaining unauthorized access to restricted parts of the website, or performing actions that they shouldn’t be allowed to.
Basically, the $hash is very weak and easy to guess. If someone can find out what it is, then they can pretend to be any user, even an administrator,
After that, they can perform actions like creating new admin accounts or accessing restricted areas.
The fact that the hash is short which never expires, and is checked loosely makes it even easier to exploit.
If you’re a WordPress user running Lite-speed Cache plugin version 6.3.0.1, then please follow these steps to reproduce the vulnerability on your local system:-
Steps to Reproduce:-
- Visit your WordPress site with the Lite-speed Cache plugin installed.
- Then, log in as a normal user using your user ID and password.
- Your browser will save your “Cred & Role” in cookies as a hashed value (e.g., #Gt%$;jhHJk*&).
- Additionally, the database stores the same hash for this user
- Next time you visit the site using the same browser, then the Lite-speed Cache plugin will retrieve the hash from your browser cookies and compare it with the hash value stored in the database.
However, If the values match, then you will gain access to your account based on your role. - An attacker can manipulate their cookies, they could set their lite-speed_role cookie to any role, including an administrative role, and set the lite-speed_hash or use brute-force techniques.
May try to match multiple hashes, or if they have information about the admin user, they might directly attempt to match the admin hash to gain access. - With 1 million possible security hash values and a rate of three requests per second, an attacker could potentially gain site access as any user ID
- Once an attacker gains access to another user’s account, such as an administrator’s, they can create a new user with administrative privileges.
For a better understanding, please refer to the diagram below:-
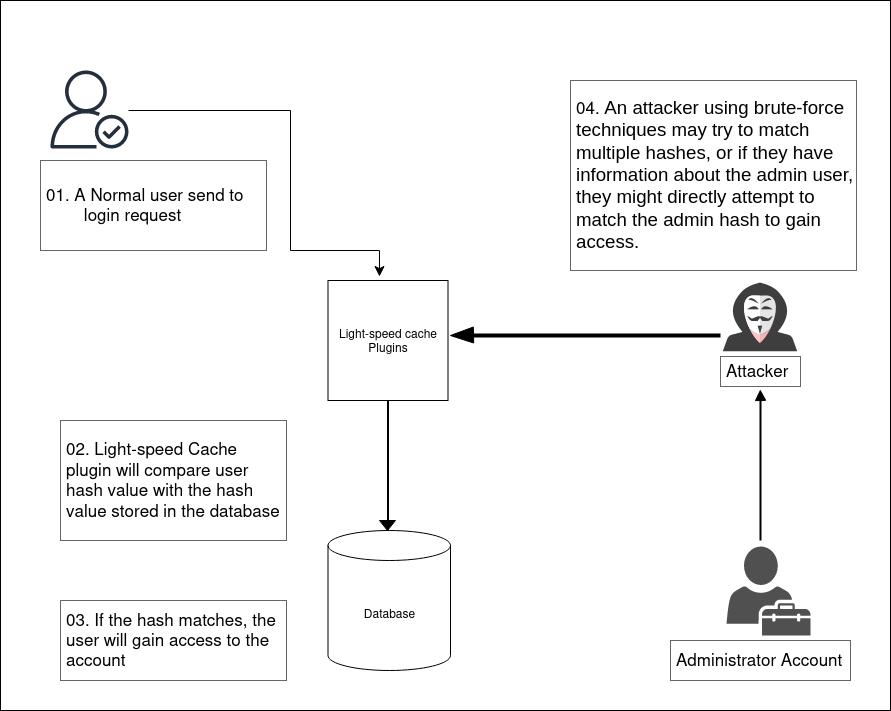
Unauthenticated Privilege Escalation
Unauthenticated privilege escalation is a security vulnerability that allows an attacker to gain higher levels of access or control over a system without needing to be authenticated or logged in.
Basically, it means that a user can exploit the system to perform actions or access data that should be restricted, even without proper credentials.
Impact
- Unauthorized Access:- Attackers can gain administrative privileges without needing to log in, which allows them to access and control the site as if they were legitimate administrators.
- Account Creation:- Attackers can create new user accounts with full administrative rights, which can further compromise the site’s security.
- Site Control:- With admin access, attackers can change site settings, install or remove plugins, modify themes, and potentially introduce malicious code or backdoors.
- Data Exposure:- Sensitive information could be accessed or leaked, including user data and configuration details.
- Reputation Damage:- If exploited, this vulnerability can damage the site’s reputation and erode user trust, especially if the site is used for business or holds personal data.
Prevention
We encourage all WordPress users to update their sites to the latest patched version 6.4.1 of Lite-speed Cache as soon as possible to ensure protection against known vulnerabilities.
Update the Plugin:- Upgrade to the latest version 6.4.1 of Lite-speed Cache where the vulnerability is fixed.
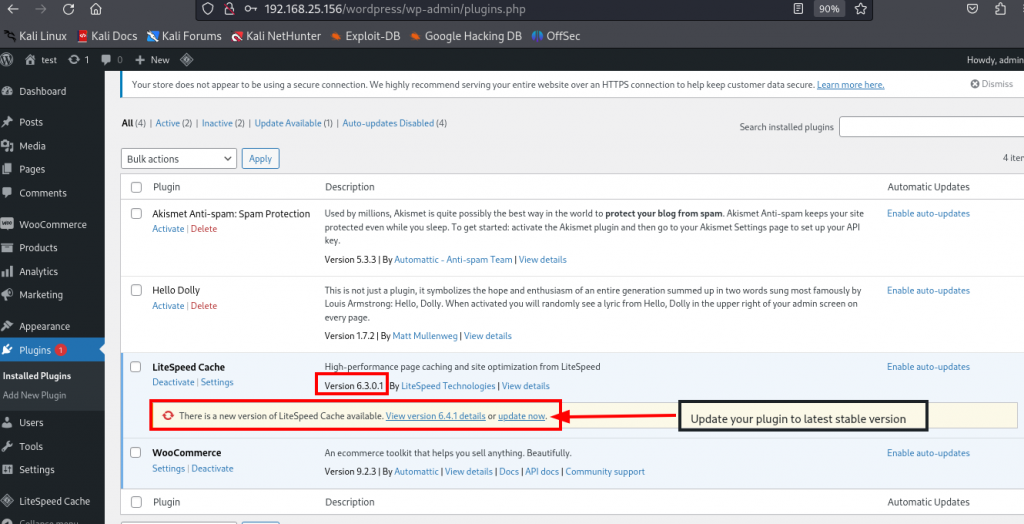
(Go to your plugin option and update Version 6.0.3.1 to 6.4.1 or higher stable version)
Restrict Access: Furthermore, Limit access to sensitive API endpoints using proper authentication and authorization mechanisms.
Monitor Logs: Regularly check debug logs for any unusual or unauthorized access attempts.
Review Permissions: Make sure that role simulation and user management features are properly restricted and validated.
Apply Security Patches: Regularly apply all security updates and patches provided by LiteSpeed or WordPress.
To patch Same version 6.3.0.1, follow these steps:-
Identify and Resolve Key Issues with These Simple Fixes
Role Simulation, None Check, Capability Check, Loose Comparison & rate_limt (Bruteforce)
Ensure that the plugin properly restricts role simulation to prevent users from setting their current ID to that of an administrator
Also, apply rate limiting on sending requests after performing any actions.
Update is_role_simulation() Function:
Open the LiteSpeed Cache plugin directory in your file manager or code editor and search for the is_role_simulation() function.
role_simulation() {
(Check if the current user has the necessary capability)
current_user_can(‘manage_options’)
If No (return false; (Unauthorized access))
}
Add a Nonce or Capability Check:
Then, modify the function to include a WordPress nonce verification (check_admin_referer()) or a capability check (current_user_can()) to ensure the function only executes for authorized users.
Check for a valid nonce to ensure the request is legitimate
if (!isset($_REQUEST[‘_wpnonce’]) || !wp_verify_nonce($_REQUEST[‘_wpnonce’], ‘role_simulation’)) { return false; // Invalid nonce }
Add strict Comparison
Further, use strict comparison methods to ensure that values match exactly and are of the expected type.
Ex:- if ($hash_from_cookie === $hash_from_database)
Please see the terminal snapshot below; this is a demo code for development purposes.
Secure async_litespeed_handler() Function:
Add proper nonce and capability checks to prevent unauthorized actions.
Go to the async_litespeed_handler() function within the plugin files.
Add Security Checks
Include a nonce check and a capability check at the beginning of the function to prevent unauthorized actions.
Update Hash Generation and Storage:
Verify that hash values used for authentication are securely generated and stored. If the hash length is short, consider using a more secure hashing algorithm or increase the length.
Review and Update Cookie Handling:
Ensure that cookies related to user sessions or role simulation are securely set. Also, use secure and HttpOnly flags for cookies to prevent unauthorized access.
Test the Changes:
After applying the patch, thoroughly test the plugin to ensure that the role simulation functionality is correctly restricted and that no unauthorized access is possible.
Deploy the Patch:
Apply the updated code to your production environment and monitor for any issues.
Prevention CheatSheet:-
https://owasp.org/www-community/controls/Blocking_Brute_Force_Attacks
https://cheatsheetseries.owasp.org/cheatsheets/Authorization_Cheat_Sheet.html
NEED HELP?
Was this guide helpful? Please share your feedback in the comments below.
In case you have any issues/queries regarding the module please raise a ticket at
https://webkul.uvdesk.com/en/customer/create-ticket/
For any further information or query contact us at [email protected].


Be the first to comment.