The WPML Multilingual CMS plugin is a popular tool used by WordPress site owners to create multilingual websites.
However, a critical security vulnerability has been identified in versions up to 4.6.12.
This vulnerability is known as an “Authenticated (Contributor+) Remote Code Execution via Twig Server-Side Template Injection,” (CVE-2024-6386). It allows an attacker to take control of your website.
In this blog, we’ll break down what this means, how this vulnerability works, and how you can protect your website.
What is the WPML Multilingual CMS Plugin
The WPML (WordPress Multilingual) Multilingual CMS plugin is a widely-used WordPress plugin designed to help website owners create and manage multilingual websites.
It allows users to translate their WordPress site content into multiple languages, and make it accessible to a global audience. Also, it has over 1 million active installations.
Understanding the Basics
Before moving to the actual Vulnerability, let’s understand some basics;
Remote Code Execution (RCE)
This is a type of security vulnerability that allows an attacker to run arbitrary code on a server or computer system from a remote location.
This is one of the most severe types of vulnerabilities because it can lead to complete control over the affected system.
RCE vulnerabilities typically occur due to flaws in software that allow user input to be improperly processed or executed by the system (Improper Input Sanitization).
Twig Server-Side Template Injection
Twig is a template engine for PHP that is commonly used to render HTML templates.
A server-side template injection is a type of vulnerability that occurs when user input is improperly handled and passed directly into a template, which is then rendered on the server.
An attacker can use this vulnerability and they can embed their malicious code inside template format.
The server interprets this code as normal code and runs the malicious command instead of just displaying the template content.
If any user input is directly passed in twig templates without any sanitization, then it will execute that directly.
For Example :
{{ 7 * 7 }} // This would calculate 7 * 7 and output 49.
The server processes this input and instead of simply displaying it as text, it interprets the code and outputs 49.
Authenticated (Contributor+)
This part means that the attacker needs to have an account on your website with at least contributor-level permissions.
A contributor can create content but needs approval to publish it. So a user must have at least a contributor account to publish content on the website.
How this Vulnerability Works
This plugin provides a shortcode ([wpml_language_switcher]) that can be used to create a custom language switcher with a Twig Template.
Then this shortcode calls a function callback () inside a plugin’s class which again calls a function render () that is used to render the Twig template supplied in the shortcode.
The lack of input sanitization makes it vulnerable to injecting malicious code into the Twig Template, which executes on the server and displays results to the client.
Due to a flaw in the WPML Plugin (up to version 4.6.12), contributors on your website could exploit the template system to execute their code on your server.
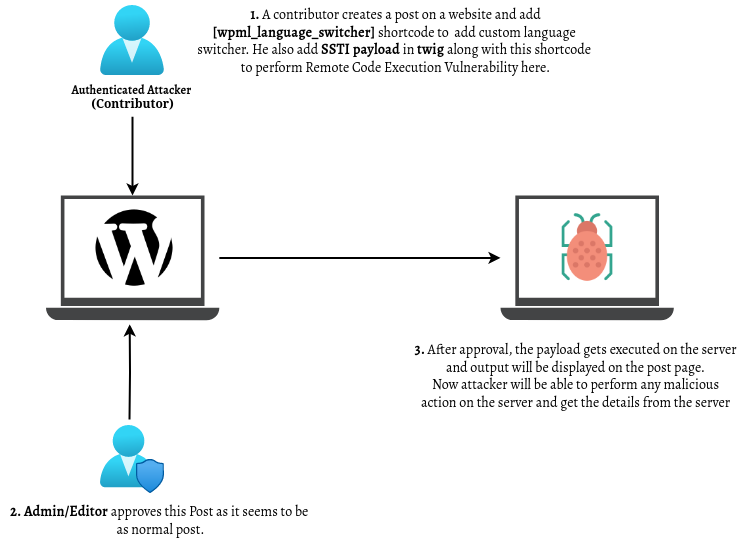
Here’s a step-by-step explanation of how an Authenticated attacker (Contributor) exploit this vulnerability;
Step 1 : Access to the System: The attacker logs in as a contributor.
Step 2 : Exploiting the Template: Suppose the contributor/attacker creates a post on your website and adds the [wpml_language_switcher] shortcode to create a custom language switcher on that post.
Then inside this shortcode, he injects malicious code/commands to perform malicious actions on the server.
He injects his malicious code in this way so it is hard to detect and then he waits to publish his post, as a contributor can write the post but not publish any post.
Step 3 : Executing Malicious Code: When any editor or administrator publishes this post, the request goes to the server.
When the server processes this template, the malicious code runs, potentially exposing sensitive data, modifying files, or creating backdoors.
By following the above steps, any attacker can execute malicious commands on the server and get the desired result.
For more understanding, refer to the below visual representation of the actual exploitation of this vulnerability.
How this Vulnerability can affect your Website
This vulnerability is particularly harmful because it combines several factors:
- The attacker needs only contributor-level access, which many websites grant to multiple users.
- Remote Code Execution is one of the most severe types of vulnerabilities, as it can lead to complete control over the website if an attacker installs a backdoor on the website.
- An attacker can modify/delete/create any file on the server by using this vulnerability.
- An attacker can get any file content using this vulnerability.
- An attacker could exploit this vulnerability without the site owner noticing until significant damage has been done.
Understanding the Security Flaw
Insufficient Input Validation
The vulnerability exists because the input that goes into the Twig templates is not properly sanitized. This allows the attacker to insert their code.
We can see the WPML Plugin’s Vulnerable Code snippet below;
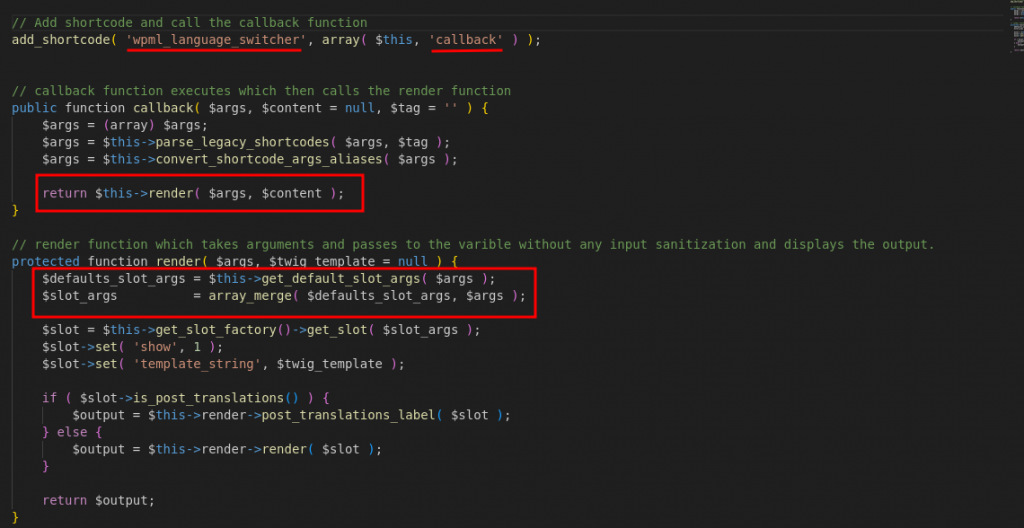
Due to a flaw in the WPML Plugin (up to version 4.6.12), contributors on your website could exploit the template system to execute their code on your server.
Permission Mismanagement
Even though contributors have limited permissions, the flaw in the system allows them to escalate these privileges and execute code.
How to protect your website from this Vulnerability
Fixing this vulnerability involves several steps:
- Update WPML Plugin: The most straightforward way to fix this issue is by updating the WPML plugin to the latest version. The developers have released patches to address this vulnerability and fix this issue in the latest version. So Update your WPML plugin to version 4.6.13 or higher.
For updating your plugin, first go to admin dashboard → plugins → WPML Multilingual CMS → Click on Update. (As shown in the below screenshot).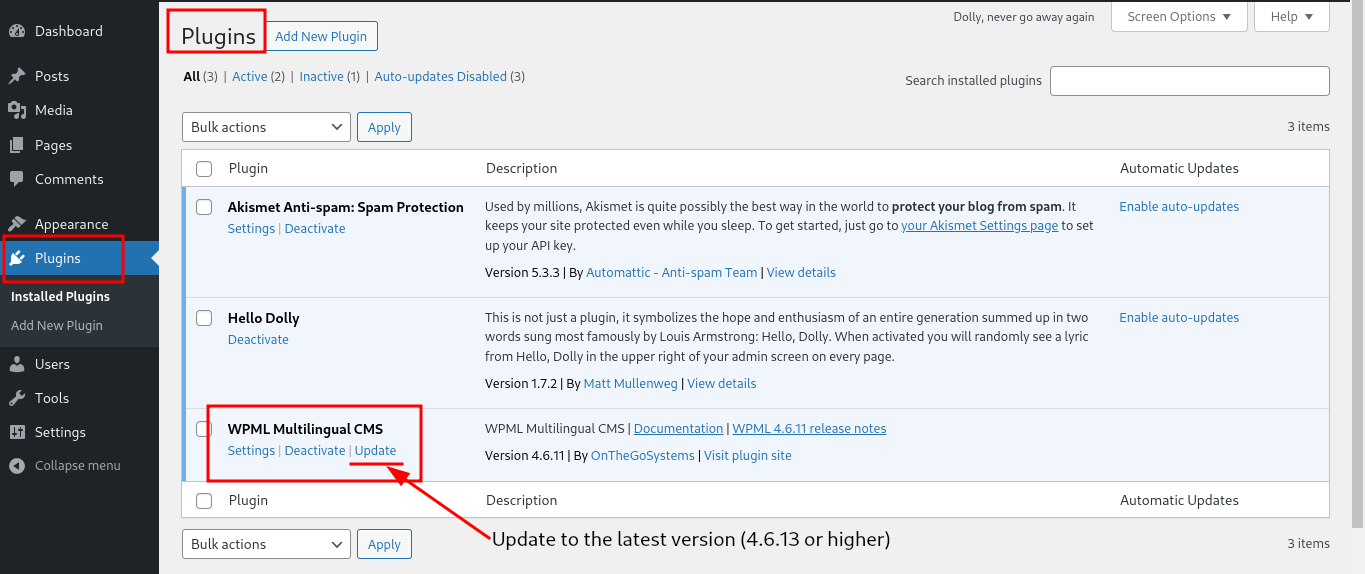
Alternatively, if the update option is not showing in your WordPress plugin section, then go to the official website of this plugin (https://wpml.org/), click on the Download button, and download the latest version of the plugin. - Limit Contributor Permissions: Consider reviewing the permissions of your contributors. Restrict their access to critical areas of the site where possible.
- Use a Web Application Firewall (WAF): A WAF can help detect and block malicious activities, including attempts to exploit this kind of vulnerability.
- Regular Security Audits: Regularly audit your website’s security to identify and fix potential vulnerabilities before they can be exploited.
Conclusion
In this blog, we have discussed the WPML Multilingual CMS Plugin Vulnerability, how this vulnerability works, the reason behind this, security flaws, and preventive measures as well.
Security Vulnerabilities like this can make a huge impact on the website and can break down the website if an attacker exploits these types of Vulnerabilities.
So We have to be aware of these types of vulnerabilities by performing regular security audits and always using updated versions of plugins.
NEED HELP?
Was this guide helpful? Please share your feedback in the comments below.
In case you have any issues/queries regarding the module please raise a ticket at
https://webkul.uvdesk.com/en/customer/create-ticket/
For any further information or query contact us at [email protected].



Be the first to comment.