
A high-severity vulnerability has been discovered in the WordPress Popular Posts plugin, which is currently active on over 100,000 websites. This flaw allows attackers to inject arbitrary shortcodes into WordPress sites without needing user accounts, posing a serious security threat.
The WordPress Popular Posts plugin is commonly used to display the most popular articles on a website. It includes caching features for better performance and an admin dashboard for tracking post popularity and engagement.
However, this newly discovered arbitrary shortcode injection vulnerability exposes websites to potential exploitation. Attackers can abuse the plugin to run unauthorized shortcodes or manipulate site content, leading to security breaches or even malware injection.
Website owners using this plugin are strongly advised to update to the latest patched version immediately or temporarily disable the plugin until a fix is confirmed. Taking prompt action will help ensure your WordPress website remains secure and protected from potential attacks.
WordPress Popular Posts Plugin Overview
The WordPress Popular Posts plugin is a highly versatile and powerful tool that allows website owners to display their most-viewed or most-discussed posts dynamically. It automatically tracks visitor interactions and ranks posts by popularity using custom algorithms, helping you highlight trending content and boost engagement.
Key Features of WordPress Popular Posts Plugin
- Multiple Widgets & Shortcodes: Easily embed popular posts anywhere on your site using widgets or shortcodes.
- Advanced Filtering: Customize your display by category, timeframe, or post type for better audience targeting.
- Built-in Caching: Improves website performance and ensures fast content delivery.
- Developer-Friendly Hooks: Offers extendable hooks and filters for advanced customization.
- Real-Time Analytics: Gain valuable visitor insights through live tracking and performance stats.
How the Plugin’s Shortcodes Work
If an admin wants to display posts based on views or comments, the plugin provides simple shortcode options:
- View-based shortcode: Fetches and displays posts with the highest number of views, ensuring that top-performing articles appear first.
- Comment-based shortcode: Highlights posts with the most user engagement by showing content with the highest comment count.
This dynamic functionality ensures that the displayed content always aligns with the chosen metric views or comments helping site owners engage visitors by showcasing trending or highly discussed posts.
Arbitrary Shortcode Injection Vulnerability
The Arbitrary Shortcode Injection Vulnerability occurs when an attacker exploits a flaw in a web application, typically in a plugin or theme of a Content Management System (CMS) like WordPress, to inject malicious shortcodes into a website.
Shortcodes are a CMS feature that allows users to insert dynamic content into posts or pages using predefined tags, like [shortcode]
Key Characteristics of the Vulnerability:
- Lack of Input Validation: The vulnerability usually stems from a lack of proper sanitization or validation of user input in functions that handle shortcode execution.
- Unauthorized Access: An attacker might exploit insufficient permission checks to insert shortcodes into content areas they should not have access to, such as admin-only pages.
Execution of Arbitrary Code: Injected shortcodes can execute server-side code, display sensitive data, or perform unauthorized actions, depending on the functionality of the shortcodes.
Identify Short-code Injection :
1. Identify Input Points:
- Locate a field or endpoint where the plugin processes user inputs, such as:
- Post or page creation areas.
- Comment sections (if enabled).
- Any feature allowing user input related to the plugin.
2. Inject Shortcodes:
- Craft a payload containing malicious shortcodes.
[popular-posts attribute=”malicious_code”] - Using curl
- curl -X POST \ -d “content=[popular-posts attribute=’malicious_payload’]” \ https://your-test-site.com/wp-json/wp/v2/posts
- Submit this payload through:
- A post/page editor.
- API endpoints, if exposed (e.g., via /wp-json).
- A form input field related to the plugin.
3. Observe Execution:
- View the content on the front end of the website or in any area where the input is rendered.
- If the vulnerability exists, the injected shortcode will execute on the server side, displaying unintended results or performing malicious actions.
4. Confirm Exploitation:
- Look for signs of successful injection, such as:
- Sensitive data is displayed on the page.
- Unexpected changes in content or layout.
- Execution of server-side commands (if RCE is achievable).
For a better understanding, please refer to the diagram below:-
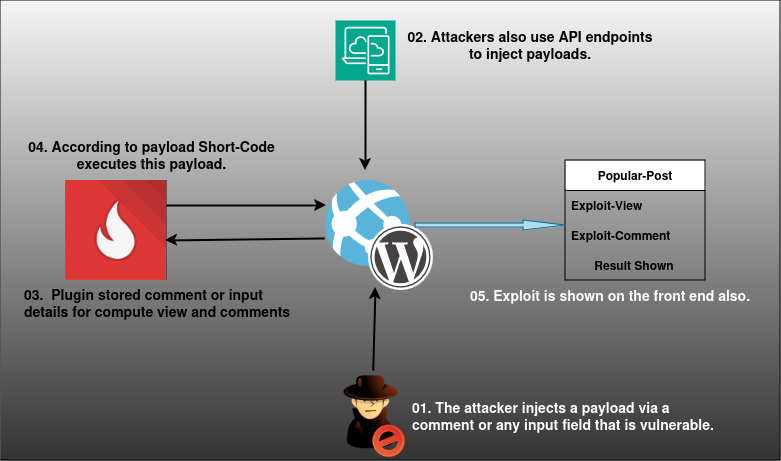
Impact of Shortcode Injection Vulnerability on Your Website:-
The Arbitrary Shortcode Injection Vulnerability in the WordPress Popular Posts plugin can lead to severe consequences, including:
- Unauthorized Actions: Attackers can modify or execute site functions via malicious shortcodes.
- Information Disclosure: Sensitive data, like user details, could be exposed.
- Malicious Content Injection: Redirection to phishing sites or loading malware.
- Remote Code Execution (RCE): Potential for attackers to execute server-side commands.
- SEO Manipulation: Injection of spammy links harms SEO and site reputation.
- Site Performance Issues: Overloading the server or causing errors.
- Reputational Damage: Loss of trust from users and potential legal liabilities.
Follow these steps to prevent your website from this vulnerability
1. Update Plugins and Themes
- Regular Updates: Always use the latest version of the WordPress Popular Posts plugin. Developers frequently release patches for known vulnerabilities.
- Enable Auto-Updates: Consider enabling automatic updates for plugins and themes to ensure timely patching.
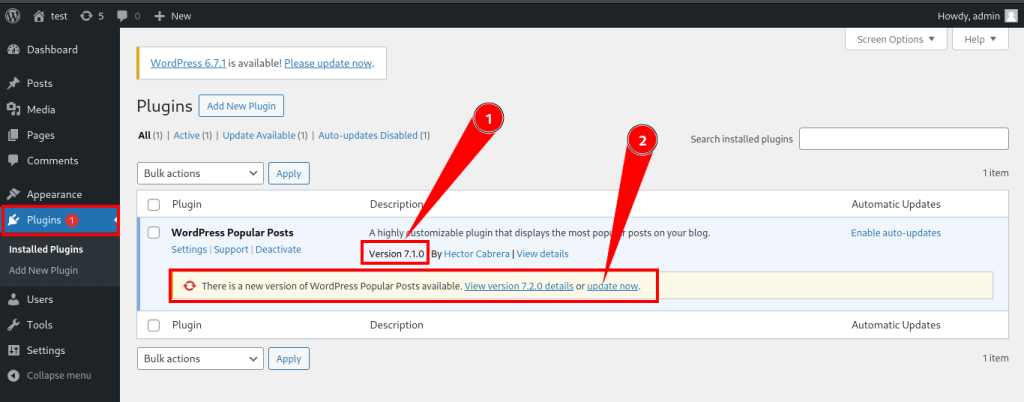
Fig:-03(Update plugin version 7.1.0 to 7.2.0 or higher version)
2. Implement Strong Input Validation
- Sanitize Inputs: Use functions like sanitize_text_field(), esc_attr(), and esc_html() to clean user inputs before processing.
- Escape Outputs: Before rendering content, escape the output using WordPress sanitization functions.
- Ensure shortcode attributes are validated with functions like shortcode_atts() to define allowed attributes.
3. Restrict Shortcode Execution
- Role-Based Access: Restrict shortcode execution to trusted user roles (e.g., administrators or editors).
- Use current_user_can() to ensure only authorized users can add or execute shortcodes.
- Disable Shortcodes for Untrusted Users:
add_filter(‘the_content’, function($content) {
if (!current_user_can(‘edit_posts’)) {
$content = strip_shortcodes($content);
}
return $content;
});
4. Disable Unused Shortcodes
Remove or disable any unnecessary shortcodes to reduce the attack surface:
remove_shortcode(‘popular-posts’);
5. Secure API Endpoints
- For REST API endpoints exposed by the plugin:
- Authentication: Ensure endpoints require proper user authentication.
- Input Validation: Validate all input received through API calls.
6. Enable a Web Application Firewall (WAF)
- Deploy a WAF like Cloudflare, Sucuri, or Wordfence to filter and block malicious requests, including shortcode injection attempts.
Conclusion:-
The Arbitrary Shortcode Injection Vulnerability in the WordPress Popular Posts plugin highlights the importance of secure coding practices and proactive website management.
This vulnerability can allow attackers to inject malicious shortcodes, leading to severe consequences such as unauthorized actions, data leakage, or even full server compromise.
Need Support?
Thank You for reading this Blog!
For further more interesting blogs, keep in touch with us. If you need any kind of support, simply raise a ticket at https://webkul.uvdesk.com/en/
For further help or queries, please contact us or raise a ticket.


Be the first to comment.