Online businesses are growing rapidly, and even a few hours of downtime in a web application can severely impact business continuity.
DDoS attack is one of the attacks that could overload your Magento 2 store and make the server unavailable to legitimate users.
Here we are going to talk about what is DDoS and how to prevent the Magento 2 store from this attack.
What is a DDoS attack?
DDoS (Distributed Denial of Service) is a type of attack that slows down or crashes our Magento 2 server, service, and networks by flooding them with fake traffic from multiple IPs.
It’s difficult to detect because the source of the traffic is not the same. DDoS attacks are a threat to all sizes of businesses.
Types of DDoS attack
1. Volumetric attack: This type of attack is a common form of DDoS attack in which the attacker consumes the target’s available bandwidth with a false data request of large size.
This traffic blocks legitimate users from accessing services and the Magento 2 server.
UDP floods in one of the volumetric attacks in which attackers overwhelm ports on the server with UDP stateless packets.
2. Protocol attack: This attack is also known as a network-layer DDoS attack. This can cause a service disruption by exploiting weaknesses in layer 3 and layer 4 of protocol stacks.
SYN flood is an example of such an attack that consumes all server resources and makes the server unavailable.
3. Application attack: It works on layer 7 of the OSI model.
This attack targets a specific web application, not an entire network, in which the attacker sends a high number of HTTP requests to exhaust the server response limit.
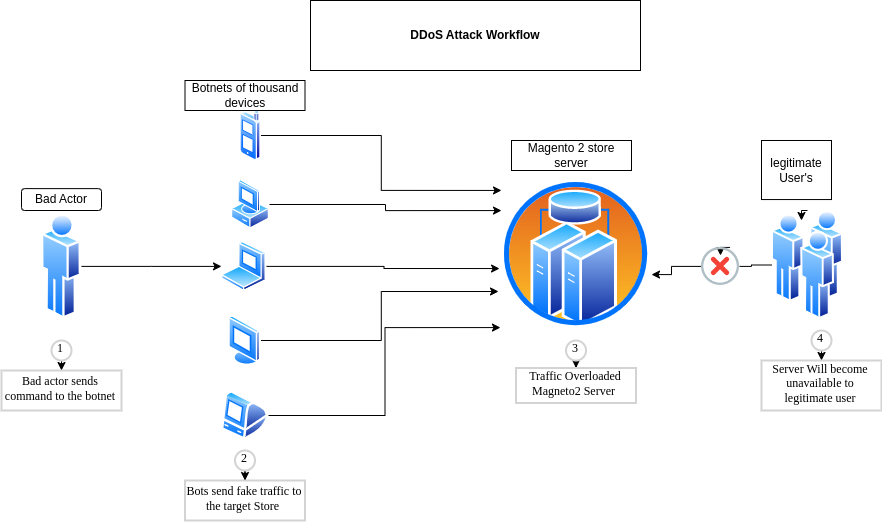
How to protect your Magento 2 server From DDoS attack:
As prevention of DDoS attacks is challenging because of the struggle to differentiate between legitimate and malicious requests.
But by taking the following countermeasures, we can mitigate the risk of DDoS attacks.
1. Using Next Generation Firewall: It filters the incoming requests at the application as well as on the network layer. This prevents bad actors from targeting your IP addresses.
Next-Generation Firewall works as an intrusion detection and prevention system, based on some rulesets to identify DDoS attacks.
2. Using AWS Shield: AWS Shield is a tool that provides protection from DDoS attacks for the application hosted on AWS. It inspects traffic in real-time and blocks harmful traffic.
3. Using CAPTCHA: Captcha is helpful in case of an attack on the authentication page.
Whenever a bot tries to process its request, it fails to pass the captcha challenge because it needs human interaction.
4. Continuous monitoring of network traffic: Monitoring traffic in real-time is a great way to trace DDoS activity and take action accordingly before the attack takes full swing.
5. Using Fail2ban Utility: Fail2ban works as an Intrusion Detection System(IDS).
It bans IPs or takes configured action on suspicious activities from server error log files such as /var/log/nginx/error.log.
Fail2ban updates the firewall rules to reject suspicious IPs from log files for a specified amount of time.
6. Request Rate Limit: Limiting the request rate is an effective way in case of a DDoS attack. This will limit the number of requests in a certain time frame based on username/IP on the login page.
Conclusion
Based on the above-given steps, we can mitigate the risk of an attack and make the store available to legitimate users.
To safeguard your Magento 2 store from DDoS attacks, visit our store and check out our DDoS firewall Protection for Magento 2 module for more details.
In case of any help or query, please contact us or raise a ticket.


2 comments