
A critical security flaw was recently discovered in the UiCore Elements WordPress plugin (≤1.3.0), which is used on over 40,000 websites, lets attackers Read Arbitrary File (LFI) on affected server.
UiCore Elements is a free Elementor addon that enhances the page builder with extra widgets, pre-built sections, and templates for easy drag-and-drop WordPress design.
So let’s understand this vulnerability, how it works, its impact on your website, and also security measures to prevent your website from this vulnerability.
What is a UiCore Elements Plugin?
UiCore Elements is a free Elementor addon designed to extend the functionality of the Elementor page builder.
UiCore Elements acts as a design booster for Elementor users, helping them save time and create visually appealing websites more efficiently.
Like other Elementor add-ons, it helps users create professional websites without coding by importing ready-made templates, sections, and extra design widgets.
What is Arbitrary File Read Vulnerability?
An Arbitrary File Read (LFI – Local File Inclusion) vulnerability happens when a web application allows a user to read files from the server that they shouldn’t normally have access to.
Normally, a website should only give access to its public files (like images, CSS, JS).
If an app accepts a user-provided filename or path without validation, an attacker can supply arbitrary paths to read sensitive server files, enabling Local File Read/Arbitrary File Read exploits.
Common target files are : wp-config.php (WordPress), Backup Files, logs, config files and other sensitive server files.
How does this Vulnerability work?
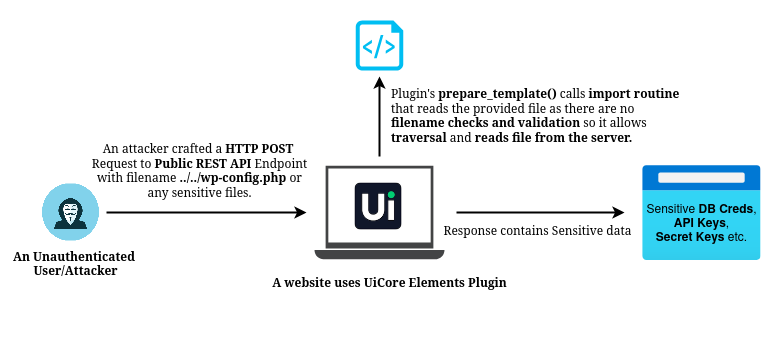
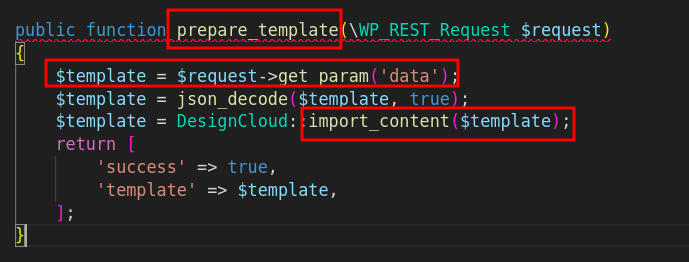
The plugin exposed a public endpoint for handling template imports that calls the prepare_template() function. Unfortunately, this endpoint lacked proper authentication and input validation.
The handler also failed to strictly validate the filename parameter. letting attackers send crafted requests to access any server file without logging in.
Since prepare_template() accepts a filename via POST request, an attacker could supply a path like ../../wp-config.php instead of a valid template or image filename to access sensitive files.
The import/template logic calls image/template import routines that read the provided path. Because validation is insufficient, the code reads the specified server file.
If the endpoint returns the file contents or an error revealing contents, the attacker obtains secrets such as DB credentials, salts, or API keys.
With those secrets, the attacker can escalate to admin privilege and perform any other malicious actions
Impact of this Vulnerability on the website
This vulnerability can cause several impacts on any websites mentioned below;
- Read database credentials from wp-config.php, connect to the DB, dump users, or reset admin passwords.
- Steal API keys and tokens stored in config or backup files.
- Deploy persistent backdoors by modifying files after gaining credentials.
- Can Access to other sites on the same host if credentials or keys are reused.
- As the endpoint was unauthenticated, the attack can be automated and mass-scanned.
What are the Security Flaws in this plugin?
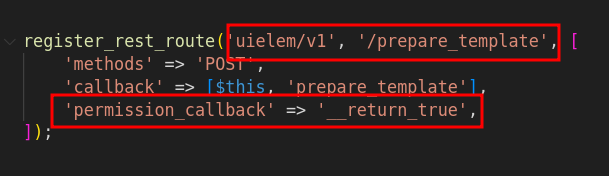
- Missing Authorization Checks :
The REST API endpoint is registered with a permission callback that returnstrue, so it has no authentication or permission checks and is publicly accessible.
- Arbitrary File Read (LFI) :
prepare_template() accepts a filename via a public endpoint with no capability checks, nonce, or filename validation—allowing unauthenticated path‑traversal to read arbitrary server files.
- Insufficient Filename Validation :
The plugin lacks filename and extension checks, allowing attackers to request local files and read their contents. - Weak Interaction with Third-party Importers (Elementor) :
UiCore’s prepare_template() uses Elementor’s import() which lacks file-type checks, letting attackers upload .php files and access sensitive data.
How to Prevent your website from this vulnerability?
To prevent your website from this vulnerability, you can follow any of the techniques mentioned below;
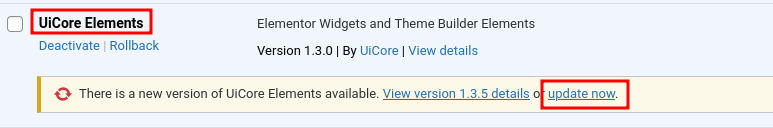
- Update UiCore Elements Plugin: Update UiCore Elements to version 1.3.1 or higher via WordPress Admin to fix the security flaw.
To upgrade to the latest version, go to WordPress Admin Dashboard → Plugins → UiCore Elements → Click on Update (As shown in the screenshot below).
Alternatively, download the latest UiCore Elements plugin from WordPress.org and upload it via the WordPress plugin upload option.
- Add Capability Check: Add administrator capability check for REST API route’s permission_callback.
- Disable Direct Access to Upload Directory: Prevent execution of scripts in upload directories by disabling direct access.
Conclusion
UiCore Elements (≤1.3.0) lacked authorization, filename checks, and safe template handling. This exposed sensitive files like wp-config.php, risking full site compromise.
This blog explains the vulnerability, its causes, and preventive measures to secure your WordPress site.
Updating to version 1.3.1 and implementing proper access controls, filename sanitization are essential to secure affected sites.
Need Help?
Was this guide helpful? Please share your feedback in the comments below.
In case you have any issues/queries regarding the module please raise a ticket at https://webkul.uvdesk.com/en/customer/create-ticket/
For any further information or query contact us at [email protected].


Be the first to comment.