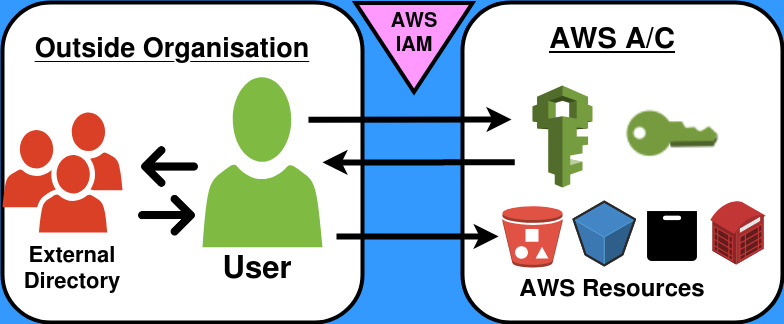
The IAM stands for identity and access management. It is a web service which controls access to AWS resources in a secure way. Consequently, IAM is used to manage authentication and authorization.
Authentication
Authentication means the validation or authentication of credentials such as username / user ID and password for identity verification.
For example, if you want to access your social media account, you’ll need to enter your credentials such as username and password. After that, verification is done to ensure that you are accessing your account or someone else is attempting it. Upon confirmation of your identity, then you are able to access your account. The entire process is called authentication. To read more just click here.
Authorization
Authorization is a method of determining the rights / privileges of access to resources, or to deciding whether an authenticated individual has access to the specific resources or not. It simply outlines the permissions of an authenticate person to access resources.
For example, When your identity (authentication) is verified in an organisation, the next move would be to determine which employee has access to which system and this is done through authorization. For more information kindly check.
Components of IAM Policy
- User – User refers to an account having associated credentials and attached permissions. ie, user specification.
- Group – It refers to the collection of IAM users.
- Policy – Policy defines the AWS resource rights and controls access. So, it clearly determines who can access it, user actions, user access grant in respect of which AWS resource etc.
- Roles – Set of permissions specifying an entity’s actions (allow or deny) in AWS console. Therefore, temporary-access users.
Features of IAM Policy
- Free Service – This service is free, and no additional costs are borne in creating accounts, groups or policies.
- Password Policy – IAM authentication policy allows password reset or rotation.
- Granular Permissions – Restrictions may apply to the specifications. For instance, you may allow users to access information, but you may restrict them to update any existing information.
- Multi-Factor Authentication – It supports MFA, that is, one-time phone authentication along with username and password.
- Shared Access – It allows creating multiple usernames and passwords, and allocating access accordingly.
- Identity Federation – It allows access to users who have already authenticated themselves from trusted parties like Facebook, Google.
- PCI DSS Compliance – This stands for Payment Card Industry Data Security Standard.For secure implementation of payment gateways. IAM abides by this norm.
Conclusion
As a result, IAM Policy helps you to manage user identities, access permissions and user control.
In case of any help or query, please contact us or raise a ticket.